Symmetric vs Asymmetric Encryption: A Detailed Comparison Guide
Encryption is a method of scrambling data so that only authorized parties can access it. There are two main techniques for encrypting data – symmetric encryption and asymmetric encryption. Both approaches have their own sets of pros and cons. This article provides an in-depth comparison between symmetric and asymmetric encryption. It examines the key differences between the two methods, analyzes the advantages and disadvantages of each, and provides guidance on when to use one versus the other. Read on to gain a comprehensive understanding of symmetric vs asymmetric encryption.
Key Takeaways:
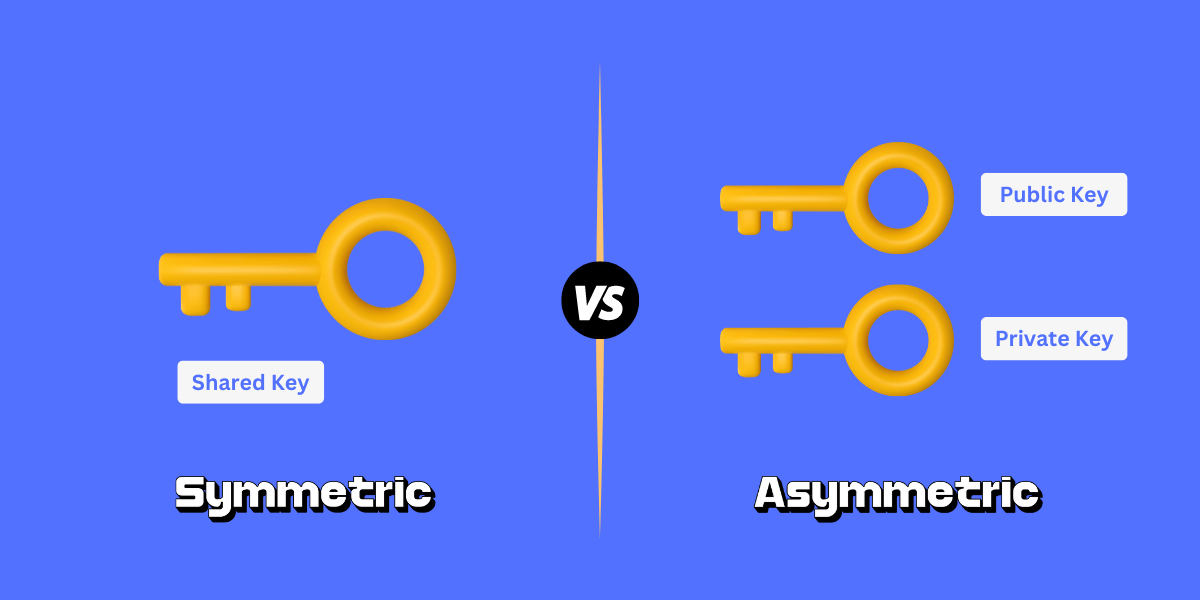
- Symmetric encryption uses a single secret key to encrypt and decrypt data, while asymmetric encryption uses a public-private key pair.
- Symmetric encryption is faster and simpler but lacks scalability. Asymmetric encryption provides better security and scalability but with slower performance.
- Symmetric encryption is ideal for bulk data encryption, while asymmetric encryption suits use cases like secure communication and digital signatures.
- Asymmetric encryption requires stronger key management since the private key must remain secret. Symmetric encryption has simpler key management with just one secret key.
- Many systems use a hybrid approach with asymmetric encryption to exchange a symmetric session key and then use the faster symmetric encryption for the data itself.
Symmetric vs Asymmetric Encryption: Key Differences
Here is a comparison summary highlighting the fundamental differences between symmetric and asymmetric encryption:
| Criteria | Symmetric Key Cryptography | Asymmetric Key Cryptography |
|---|---|---|
| Keys Used | Single secret key | Public and private key pair |
| Key Exchange | Secret key must be transmitted or pre-shared | Only public key needs to be shared |
| Security Model | Relies on key secrecy | Relies on mathematical relationship between key pairs |
| Computational Efficiency | Very fast | Relatively slow due to mathematical complexity |
| Scalability | Not very scalable | Highly scalable for multiple users |
| Non-Repudiation | Not supported | Supports capabilities like digital signatures |
| Key Management | Simple with single shared key | Complex with public/private key pairs |
| Use Cases | Bulk data encryption, storage, network transmission | Secure communication, digital signatures, authentication |
Symmetric Encryption Overview
Symmetric encryption, also known as shared key or secret key encryption, uses a single secret key to encrypt and decrypt data. The sender uses the secret key to encrypt the plaintext and sends the ciphertext to the recipient. The recipient applies the same secret key to decrypt the message and retrieve the plaintext.
Some examples of symmetric encryption algorithms include:
- Data Encryption Standard (DES)
- Triple DES (3DES)
- Advanced Encryption Standard (AES)
- Blowfish
- Twofish
- Rivest Ciphers (RC4, RC5, RC6)
Since the same key encrypts and decrypts the data, symmetric encryption is straightforward and efficient in terms of computation. The symmetric algorithms tend to be faster and use less processing power compared to asymmetric algorithms.
Advantages of Symmetric Encryption:
- Faster performance and lower computational overhead since encryption and decryption use the same simple algorithm.
- Simpler key management since only one secret key needs to be exchanged between entities.
- Suits applications with high data throughput like storage encryption, network communications, and embedded systems.
- Provides confidentiality for data-at-rest and data-in-transit use cases.
Disadvantages of Symmetric Encryption:
- Lacks scalability since each pair of communicating entities must exchange keys securely. Doesn’t work well for large networks.
- Key distribution is a challenge since the same key is used for multiple purposes. The key must be transmitted or exchanged via a secure channel.
- It is not suitable for non-repudiation requirements like digital signatures and authentication since the single key is shared.
- Brute force attacks can theoretically be used to crack the key, especially for weaker algorithms with small key sizes.
In summary, symmetric encryption provides fast and simple data encryption and confidentiality. But the single shared key raises challenges for large scale deployment and applications needing stronger security like authentication and non-repudiation.
Asymmetric Encryption Overview
Asymmetric encryption, also known as public key encryption, uses a pair of keys – a public key and a private key for encryption and decryption. The public key is made openly available and can be used by anyone to encrypt messages. But the private key is kept secret and is used only by the recipient to decrypt the ciphertext.
Some examples of asymmetric algorithms:
- Rivest–Shamir–Adleman (RSA)
- Elliptic Curve Cryptography (ECC)
- Diffie-Hellman Key Exchange
- Digital Signature Algorithm (DSA)
Since the keys are different, asymmetric encryption introduces more computational complexity. Encryption and decryption take longer than symmetric algorithms. However, the use of mathematically linked public and private key pairs provides stronger security and additional capabilities.
Advantages of Asymmetric Encryption:
- Provides a scalable solution for secure communication between multiple entities without prior exchange of secrets.
- Enables non-repudiation capabilities like digital signatures, authentication, and identity verification.
- Private keys can be kept completely secret, allowing stronger encryption with larger key sizes.
- Public keys can be openly shared, enabling decentralized, secure communication between strangers.
- Supports key and privilege management for multi-user environments.
Disadvantages of Asymmetric Encryption:
- Slower performance and higher computational overheads due to mathematical complexity.
- Generally, higher resource requirements for key generation, storage, and management.
- Potential vulnerability to attacks against the mathematical properties of the keys.
- Private keys must be kept absolutely secret and securely backed up to prevent irrecoverable data loss.
In summary, asymmetric encryption provides enhanced security, scalability, and capabilities like digital signatures. However, the performance overhead and key management responsibilities are higher.
When to Use Symmetric vs Asymmetric Encryption
So, when should you use symmetric encryption versus asymmetric encryption? Here are some general guidelines:
- Symmetric encryption is used for simple data encryption and confidentiality for data at rest or in transit. The high speed and low overhead suit bulk data encryption needs like encrypted file storage, full disk encryption, and VPN tunnel encryption.
- Use asymmetric encryption for establishing secure communications between multiple parties that don’t share secrets a priori. The scalability suits public key infrastructures, SSL/TLS connections, encrypted email, cryptocurrency wallets, and blockchain transactions.
- Use asymmetric encryption for capabilities requiring non-repudiation like digital signatures, identity verification, authentication, and key exchange. The private key enables these cryptographic assurances.
- Use a hybrid approach with asymmetric encryption to exchange a temporary symmetric session key and then leverage fast symmetric encryption for the actual data exchange. This provides performance benefits while maintaining security.
- Evaluate algorithm strength, key sizes, known vulnerabilities, and compliance considerations like FIPS 140-2 to determine the right symmetric or asymmetric algorithm for your specific needs.
Final Thoughts
In summary, asymmetric encryption generally provides stronger security properties, while symmetric encryption optimizes performance and simplicity. Understanding their relative strengths allows for the right approach. Many systems also blend both techniques to enjoy the best of both worlds.
Frequently Asked Questions
What is the main difference between symmetric and asymmetric encryption?
The main difference is that symmetric encryption uses only one secret key for both encryption and decryption, while asymmetric encryption uses a public-private key pair with distinct keys.
Is symmetric or asymmetric encryption more secure?
Asymmetric encryption is generally considered more secure since the private key remains completely secret. However, sufficiently long symmetric keys can also provide robust security. The algorithm, key size, and implementation impact overall security for both approaches.
Why is symmetric encryption faster than asymmetric encryption?
Symmetric algorithms involve simpler mathematical operations like substitution and transposition using the same key. Asymmetric encryption relies on complex mathematical transformations using the linked but distinct public and private keys. This added complexity causes slower performance.
What are the typical key sizes for symmetric and asymmetric encryption?
Symmetric algorithms typically use key sizes between 128 to 256-bit keys or larger. Asymmetric algorithms start from 1024-bit keys and often use 2048-bit or 4096-bit keys for better security. The larger key sizes contribute to slower performance.
Can you explain hybrid encryption?
Hybrid encryption combines the best aspects of symmetric and asymmetric encryption. It uses asymmetric encryption to exchange a random symmetric session key and then uses the faster symmetric encryption with this temporary key to encrypt the actual message data.
What are some examples of symmetric encryption algorithms?
Common symmetric algorithms include AES, DES, 3DES, RC4, RC5, RC6, Blowfish, Twofish, etc. AES is the widely used symmetric encryption standard today, superseding DES.
What are some examples of asymmetric encryption algorithms?
Popular asymmetric algorithms include RSA, ECC, Diffie-Hellman, ElGamal, and DSA. RSA is the most widely deployed today, while ECC offers better efficiency.
When should I use symmetric vs asymmetric encryption?
Use symmetric encryption for bulk data protection at rest/transit requiring high speed. Use asymmetric encryption for secure communication between multiple parties and capabilities like digital signatures. A hybrid approach provides the best of both.