DoS and DDoS Attacks: Differences and How to Prevent
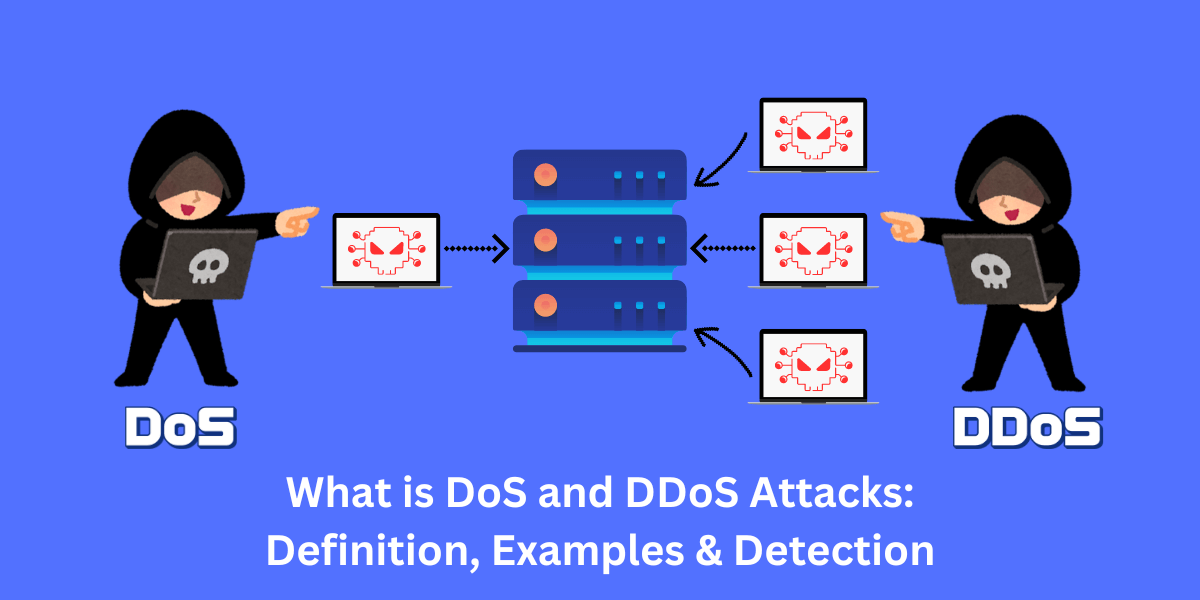
A Denial of Service (DoS) attack is a cyber attack that aims to make a website or online service unavailable by overwhelming it with traffic from a single source. A Distributed Denial of Service (DDoS) attack does the same thing but uses multiple connected devices to flood the target. DoS and DDoS attacks are common threats that have taken down major websites and online services, from banks to government institutions. These attacks are relatively easy to execute and are increasingly being used as protest tactics by hacktivist groups.
In this comprehensive guide, we’ll cover everything you need to know about DoS and DDoS attacks, including:
- The difference between DoS and DDoS
- Common DDoS attack methods
- Major DDoS attacks in history
- The impact and cost of DDoS attacks
- How to detect and defend against them
Understanding these powerful weapons of disruption is key for any individual or organization with an online presence. Let’s dive in.
Key Takeaways:
- DoS (Denial of Service) and DDoS (Distributed Denial of Service) attacks aim to flood a website or online service with traffic and make it unavailable.
- DoS attacks come from one source, while DDoS attacks involve multiple connected devices.
- Common DDoS attack methods include DNS amplification, SYN floods, UDP floods, and HTTP floods.
- DDoS attacks can be mitigated through blacklisting IP addresses, rate limiting, upstream filtering, and DDoS protection services.
- Maintaining redundancy, autoscaling, and having an incident response plan can help minimize the impact of an attack.
DoS vs. DDoS Attacks: What’s the Difference?
Although a DoS attack and a DDoS attack may have similar end goals, they work in slightly different ways.
DoS Attacks
A DoS attack involves sending a flood of requests from a single source, like one computer or internet connection. This overload of traffic exhausts the resources on the target server and can crash the system, making the website or service inaccessible.
Common DoS attack types include:
- Ping flood: Sending a huge volume of ICMP echo request (“ping”) packets to the target.
- SYN flood: Sending a stream of TCP SYN packets to a server without completing the handshake, overwhelming its connection queue.
- UDP flood: Inundating random ports on the target with User Datagram Protocol (UDP) packets.
- HTTP flood: Barraging the web server with valid HTTP GET or POST requests.
- Slowloris: Opening multiple connections and slowly sending partial HTTP requests to hold them open.
- Buffer overflow: Causing a service crash by sending malformed data that overflows an application buffer.
The main downside of DoS attacks is that they’re relatively easy to block by blacklisting the single sending IP address. However, they can still be difficult to fully mitigate and often succeed in disrupting availability.
DDoS Attacks
A DDoS (distributed denial of service) attack uses multiple connected devices to overwhelm the target. Instead of coming from one source, the attack traffic originates from many distributed sources.
This offers several advantages:
- Increased scale: With hundreds or thousands of unique IP addresses attacking concurrently, DDoS attacks can generate massive volumes of traffic that most networks can’t handle.
- Difficult to block: Blacklisting single IP addresses does nothing against a widespread botnet DDoS attack. The distributed nature makes it much harder to filter based on source.
- Obfuscated origin: DDoS traffic is often spoofed or relayed through proxies, hiding the true attack source while appearing more legitimate.
- Lower cost: Renting a DDoS botnet service is inexpensive compared to the damage it can inflict. Some botnets even allow “free trial” DDoS attacks.
DDoS attacks require some technical skills to coordinate, but open-source tools like LOIC make it feasible for anyone. Next, we’ll look at the most common DDoS attack vectors that were exploited today.
Common DDoS Attack Vectors and Methods
Cybercriminals have many techniques up their sleeve when executing a DDoS assault. Here are some of the most prevalent DDoS attack vectors:
Volume-Based DDoS Attacks
Volume-based DDoS attacks aim to overwhelm the target’s bandwidth by saturating their pipe with a deluge of traffic. Some of the main volumetric attack types include:
- UDP flood: Barraging random ports on the target with UDP datagrams (packets), consuming available bandwidth.
- ICMP flood: Flooding the victim with ICMP echo requests (pings) that overload network capacity.
- DNS amplification: Spoofing the target’s IP address in DNS lookup requests sent to open DNS resolvers, which send large responses to the target.
- NTP amplification: Exploiting publicly accessible NTP servers to reflect monstrous UDP traffic volumes to the spoofed target IP.
- Memcached amplification: Abusing unsecured Memcached servers to trigger large data payloads sent to the target.
- SNMP amplification: Spoofing the target IP in SNMP requests to SNMP managers configured to send big trap messages to the forger IP.
Volume-based attacks work by clogging up the target’s internet pipe with junk traffic, making it impossible to handle legitimate requests.
Protocol Attacks
Protocol attacks consume actual server resources vs. just bandwidth, opening up vectors like:
- SYN flood: Rapidly sending TCP SYN packets to use up all available connections in the SYN-RCVD queue.
- ACK flood: Transmitting spoofed ACK responses for requests that weren’t sent, confusing TCP sequencing.
- HTTP flood: Inundating web servers with valid HTTP GET or POST requests from spoofed IPs.
- Slowloris: Slowly dripping partial HTTP requests to monopolize Apache server threads.
Well-crafted protocol attacks can starve backend resources like sockets, connection queues, and threads – not just saturate the front-end pipe.
Application Layer DDoS Attacks
Application layer attacks target web server resources and backend application logic:
- HTTP request flooding: Overwhelming dynamic application logic with valid HTTP requests.
- Session flooding: Start and interrupt many application sessions to exhaust session resources.
- SQL injection: Causing database query spikes via malicious SQL injection payloads.
- Cross-site scripting (XSS): Launching XSS exploits against vulnerable apps to spread browser-based botnets.
App-layer DDoS attacks don’t require massive volumes. They exploit vulnerabilities in web apps and servers through precise, low-volume attacks.
Reflection & Amplification DDoS
Reflection and amplification attacks use innocuous public servers to help bombard the victim unwittingly:
- The attacker spoofs the target’s IP address in a query sent to an open DNS resolver, NTP server, Memcache server, etc.
- The server responds as expected by sending a large reply to the forged IP address (the spoofed target).
- Using many servers multiplies the attack bandwidth that can be directed at the target.
DNS and NTP are common protocols exploited for DDoS reflection attacks due to the large responses they generate. However, the risk exists for any UDP-based protocol that replies with more data than the request.
Permanent vs. Conventional DDoS
Permanent denial-of-service (PDoS) attacks do long-lasting damage versus just temporary disruption:
- Firmware attacks can brick IoT devices completely.
- Damaging unprotected servers by overwriting OS files or data.
- Using up cloud computing resources budgeted monthly.
- Getting blacklisted by vendors as an attacker.
PDoS effects can linger long after the attack traffic stops, so cyber criminals use PDoS more sparingly due to its lasting impact.
Understanding the plethora of DDoS vectors is key to mitigating the risk they pose and selecting proper defenses. Now, let’s look back at major historical DDoS attacks.
Major DDoS Attacks in History
Distributed denial-of-service attacks have grown exponentially larger over the past decade. Here are some of the biggest DDoS attacks on record:
- February 2000 – Major sites, including Amazon, CNN, eBay, and Yahoo! were battered by DDoS attacks topping out at 1 Gbps. This early demonstration showed the disruption attackers could inflict on the growing internet.
- October 2002 – The 13 DNS root servers that handle web address lookups worldwide were DDoSed with up to 4 Gbps each, temporarily disrupting service for most internet users. The perils of key internet infrastructure dependence became clear.
- July 2009 – patriotic hacking groups launched politically motivated DDoS attacks peaking at 60 Gbps against government sites in the U.S. and South Korea over several days, disrupting operations.
- December 2010 – Online whistleblower WikiLeaks was subject to a sustained DDoS attack exceeding 100 Gbps after releasing controversial secret documents provided by Chelsea Manning.
- September 2012—The launch of the itsoknoproblembro DDoS toolkit gave script kiddies an easy way to rent massive DDoS botnets, enabling the “DDoS as a service” business model.
- March 2013 – The largest DDoS attack recorded at the time peaked at 300 Gbps using DNS reflection, taking down anti-spam service Spamhaus. Cyberbunker launched the attack after being blacklisted by Spamhaus.
- January 2014 – Hacktivist group Lizard Squad’s DDoS attacks against Xbox Live and Playstation Network disrupted online gaming services. They issued bomb threats to divert an American Airlines plane carrying Sony Online CEO John Smedley.
- September 2016 – The Mirai botnet executed the then-largest DDoS attack against journalist Brian Krebs’ website, reaching 620 Gbps and knocking his site offline.
- October 2016 – Mirai went on to be used in the biggest DDoS ever measured – an IoT-powered 1.2 Tbps assault on Dyn DNS servers that knocked major sites like Twitter, Netflix, Reddit, and Airbnb offline.
- February 2018 – Hackers overwhelmed GitHub servers with the most intensive bandwidth attack recorded at that point, peaking at 1.35 Tbps. The Memcached reflection attack exploited unsecured Memcached systems exposed to the internet.
- June 2019—Imperva Incapsula mitigated 470 million packets per second (Mpps) DDoS attack, one of the fiercest ever in terms of packet rate vs. bandwidth volume. The 39.927 Gbps UDP floods nearly took a North American ISP down.
- June 2021—Cloudflare reported blocking an HTTP DDoS that topped a record-setting 17.2 million requests per second (RPS). While not bandwidth-intensive, it showed the power of botnets to clobber servers through app-layer attacks rather than just bandwidth flooding.
DDoS incidents continue escalating in size, frequency, and creativity. With the advent of botnet rentals, any grievance-holder can launch powerful attacks for a nominal fee. Understanding the history provides context on how DDoS tactics have evolved and why defenses must continually adapt to match.
The Cost & Impact of DDoS Attacks
The business impact of DoS and DDoS attacks can be severe:
- Revenue loss: Site downtime and inability to transact prevents revenue generation, with massive losses possible for major ecommerce companies.
- Reputational damage: Users lose trust after being unable to access services, while brands look inept after a successful attack.
- Productivity loss: Staff are unable to perform duties online, communications are disrupted, and focus shifts to incident response.
- Incident response costs: Diverting staff to attack mitigation, deploying third-party filtering services, forensic analysis, and PR all burn budget.
- SLA violations: Downtime incurred during an attack can breach service-level agreements with customers.
- Compliance issues: Interruptions may violate regulatory requirements around service availability and data access.
- Ransom demands: Extortionists increasingly threaten DDoS attacks against organizations if the ransom isn’t paid, posing dilemmas.
According to IDC Research, the average cost of infrastructure downtime from a DDoS attack is around $250,000 per hour – a heavy toll for mid-size and large organizations.
Beyond financial impacts, attacks can also have major indirect effects:
- Recruitment difficulties: After high-profile attacks, skilled tech talent may be deterred from joining a company perceived as insecure.
- Loss of user trust: Users whose personal info is compromised in an incident may permanently take their business elsewhere.
- Embarrassment and poor PR: Media coverage highlights the victim’s inability to defend himself, causing public embarrassment.
- Security scrutiny: High-impact attacks prompt regulators and auditors to enhance security requirements and oversight.
- Increased cyber insurance costs: Carriers see heightened risk after incidents and raise premiums as a result.
DDoS attacks can have long-lasting ripple effects even after services are restored. For mission-critical providers like banks, the existential threat may even drive acquisition – processing giant FIS bought Worldpay after cybersecurity risks from two 2018 DDoS attacks worried investors.
The potential for outsized damage explains why DDoS defense must be a top priority. Next, we’ll explore ways to detect and mitigate these stealthy attacks.
DDoS Attack Detection & Defense Strategies
Defending against DDoS confronts unique challenges. Because traffic appears to come from legitimate sources and mimics normal access patterns, intrusion detection can be avoided. And with attacks flooding in at 100+ Gbps, traditional firewalls and filters are like a garden hose against a fire hydrant.
But a layered model combining multiple techniques can effectively minimize the impact:
Network Behavior Analysis
One way to sense a possible DDoS event is to look for traffic anomalies and sudden spikes outside normal baselines. Tools like Snort and Bro can analyze network flow patterns and raise alerts on abnormal behavior. Statistical analysis and machine learning add smarts to model typical traffic adaptively.
The downside is that many DDoS attacks now ramp up slowly and look more like organic growth. Sophisticated botnets will even mimic human traits like mouse movements and clicks to act “normal.” So, network behavior analysis can’t catch every attack.
Blackhole Route Filtering
When a DDoS attack is detected, blackholing or null routing the malicious traffic is an effective reactive strategy. This strategy relies on BGP flowspec rules that silently discard all traffic from specific subnet sources, alleviating the load on your infrastructure.
Blackhole filtering is applied upstream by your internet service provider, so it blocks junk traffic before it even hits your network perimeter. This has become the standard first line of defense during volumetric DDoS events.
Rate Limiting
Setting thresholds to only allow a certain number of requests per second or megabits per second from a given source is another simple frontline filtering technique. Rate limiting caps traffic volumes based on source IP and other attributes.
This method helps prevent aggressive spikes from any single source from overwhelming your systems. But it must be tuned carefully to avoid blocking legitimate users – a tricky balancing act.
Upstream Scrubbing
For mid-size organizations, the most scalable defense against massive distributed attacks is to divert traffic to DDoS scrubbing services offered by upstream ISPs and providers like Cloudflare.
These systems absorb the malicious traffic on your behalf while passing only cleansed traffic onto your network and data centers. Major internet backbones peer these services directly for efficient mitigation of high-volume floods.
The downsides are additional latency from the diversion and bandwidth and subscription costs incurred during every attack.
On-Premises Scrubbers
For large enterprises and cloud networks, investing in on-premises DDoS scrubbing hardware like Radware or Arbor can be cost-effective. These filter out known garbage traffic while dynamically blocking suspect sources through behavioral modeling.
Scrubbers protect applications by sitting between your internet border routers and backend servers. Unlike upstream filtering, this avoids any latency penalty or bandwidth fees. However, it involves considerable capital expense to handle the biggest botnet attacks.
Web App Firewalls
Specialized layer 7 Web Application Firewalls (WAFs) provide deep inspection of HTTP/S traffic and actively combat app-layer DDoS techniques like HTTP flooding and Slowloris.
By understanding application-level protocols and user behavior, WAFs can filter out requests intended to overwhelm application logic. They can also detect and thwart SQL injection, cross-site scripting, and other exploits.
Overprovision Bandwidth
Another proactive strategy is to massively overprovision bandwidth at the data center and network edges. This ensures your connectivity capacity dwarfs most DDoS attack volumes, avoiding chokepoints under load.
Overprovisioning requires closely tracking growth in attack sizes and expanding capacity accordingly. While capital-intensive, it reduces reliance on reactive controls like blackholing and scrubbing. The scale of leading cloud providers makes this approach viable.
Combining preventive tools, proactive capacity planning, and reactive filtering techniques helps create a formidable anti-DDoS defense. However, minimizing exposure through resilient architecture is also crucial.
Optimizing Architecture for DDoS Resilience
The way systems and infrastructure are architected also influences DDoS resilience:
Minimize Single Points of Failure
Dependence on individual servers, data centers, and network links creates dangerous bottlenecks. Distributing traffic across geographically dispersed infrastructure prevents outages when one node goes down.
Build in Redundancy
Excess capacity and duplicate components mean one failure doesn’t cascade through the entire environment. Multiple connections, spare servers, and contingency sites prevent disruption.
Autoscale Resources
Cloud platforms allow programs to instantly scale up servers, bandwidth, and services to handle spikes induced by DDoS surges and maintain performance. Adding capacity dynamically helps counter demand floods.
Use Load Balancing
Distributing application traffic across multiple servers increases aggregate horsepower. This makes it harder to overload individual components and helps withstand demand spikes.
Limit Cardinality
Restrict the number of resources per entity and client, such as connections, queries, and files. Capping consumption makes it harder for any single source to exhaust capacity. This requires tuning to avoid limiting legitimate users.
Always-On DDoS Mitigation
Keep base-level defenses like WAFs and scrubbing active at all times instead of waiting for detected events. This prevents lower-level attacks from causing damage before they intensify.
Optimizing architecture for elasticity, redundancy, and reduced cardinality makes applications inherently more DDoS resilient. But contingency planning is also key.
Incident Response & Contingency Planning
The right contingency plan minimizes disruption when DDoS strikes:
- Have an emergency response plan – Document steps to rapidly assess impact, alert stakeholders, activate defenses, and restore functionality. Practice responding to simulated attacks.
- Maintain spare capacity – Keep surplus bandwidth, computing resources, and data center space available to handle traffic spikes during attacks without overloading production.
- Consider upstream scrubbing – Contract with ISP/cloud DDoS filtering services to divert and cleanse inbound traffic readily during large events.
- Have manual failovers planned – Be ready to shift usage to alternative sites and providers in case automation fails.
- Regularly back up critical data – Ensure there is no data loss if attacks damage or corrupt databases and servers.
- Stay vigilant 24/7 – Monitor networks diligently even during off-hours since many attacks occur at night and on weekends to maximize disruption.
- Communicate status proactively—Use status pages to Keep stakeholders, customers, and the public informed of issues, progress, and restoration ETA.
- Simulate scenarios – Preemptively run through response procedures and uncover gaps through practice DDoS drills.
Having mitigation capabilities and contingency options ready before an actual DDoS attack is key to minimizing their damage.
Final Thoughts
Distributed denial of service represents one of the hardest cybersecurity challenges today due to the virtually unlimited attack surface and difficulty tracing perpetrators.
DDoS botnets continue to grow in power while new vectors like cracked IoT devices and server amplifiers allow higher volumes. Meanwhile, motivations have expanded beyond activists to include nation-states and cybercriminals.
However, a solid understanding of the common DDoS techniques and vectors makes it possible to architect networks and deploy countermeasures to minimize disruption. Ongoing vigilance and adaptation are crucial to detect and halt emerging attack methods.
Specific steps, such as implementing layered defenses, maintaining spare capacity, diverting traffic through scrubbing services, eliminating chokepoints and single points of failure, and testing incident response plans, can help nullify most attacks.
While the asymmetric economics ensure DDoS cannot be fully prevented, proper persistence planning, proactive architecture optimizations, and layered mitigations can help drastically reduce risk exposure.
Companies operating digital assets must prioritize keeping infrastructure available, making online services accessible, and protecting customer data.
Frequently Asked Questions
Still have questions about DDoS attacks and how to stop them? Here are answers to some frequently asked questions:
What is the most common DDoS attack method?
Volumetric network flooding attacks are still the most prevalent, aiming to clog up internet connectivity with junk traffic. UDP and ICMP floods, along with amplification via DNS and NTP servers, are commonly used here.
How long do DDoS attacks last?
Attack duration varies widely from a few minutes to weeks, depending on the perpetrators’ motivations and resources. Political activist attacks often last less than an hour, while nation-state and cybercrime attacks can persist for days to inflict maximum pain.
What’s the difference between a DDoS and a DoS attack?
A DoS originates from one source, while a DDoS uses a botnet of thousands of devices to attack from multiple locations simultaneously. DoS is easier to block, but it can overwhelm most networks.
How do you detect a DDoS attack?
Sudden spikes in bandwidth utilization, packets per second, and abnormal traffic flows signal possible attacks. However, low-and-slow attacks mimic normal patterns, so behavioral analysis and machine learning are also required for reliable detection.
How can attacks be traced to their source?
IP spoofing and reflective techniques make tracing difficult. However, forensics of packet structures, behavioral patterns, and botnet C&C communication can sometimes reveal origins after extensive analysis. Attributions are still rare.
What are the legal consequences of DDoS attacks?
Participating in DDoS attacks or renting botnets for them can lead to criminal charges and prison time. Loosely organized groups like Anonymous make perpetrators hard to prosecute.
How can organizations prepare for DDoS attacks?
Baseline network patterns, implement layered defenses, overprovision capacity, eliminate single points of failure, create DDoS response plans, maintain spare resources, and arrange scrubbing services before attacks occur.
Can DDoS attacks be entirely prevented?
With enough resources and preparation, the impact of most DDoS attacks can be minimized, but it’s impossible to block every attack vector. Ongoing vigilance and adaptation to emerging methods are key to risk reduction.

Jinu Arjun
 Verified Experienced Content Writer
Verified Experienced Content Writer
Jinu Arjun is an accomplished content writer with over 8+ years of experience in the industry. She currently works as a Content Writer at EncryptInsights.com, where she specializes in crafting engaging and informative content across a wide range of verticals, including Web Security, VPN, Cyber Security, and Technology.