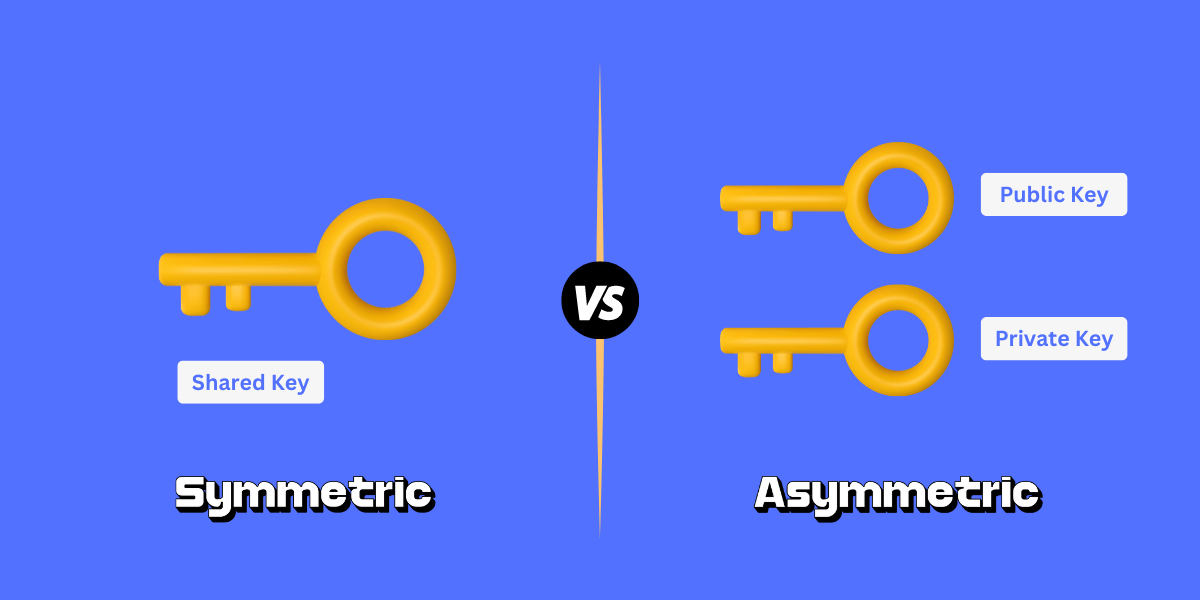
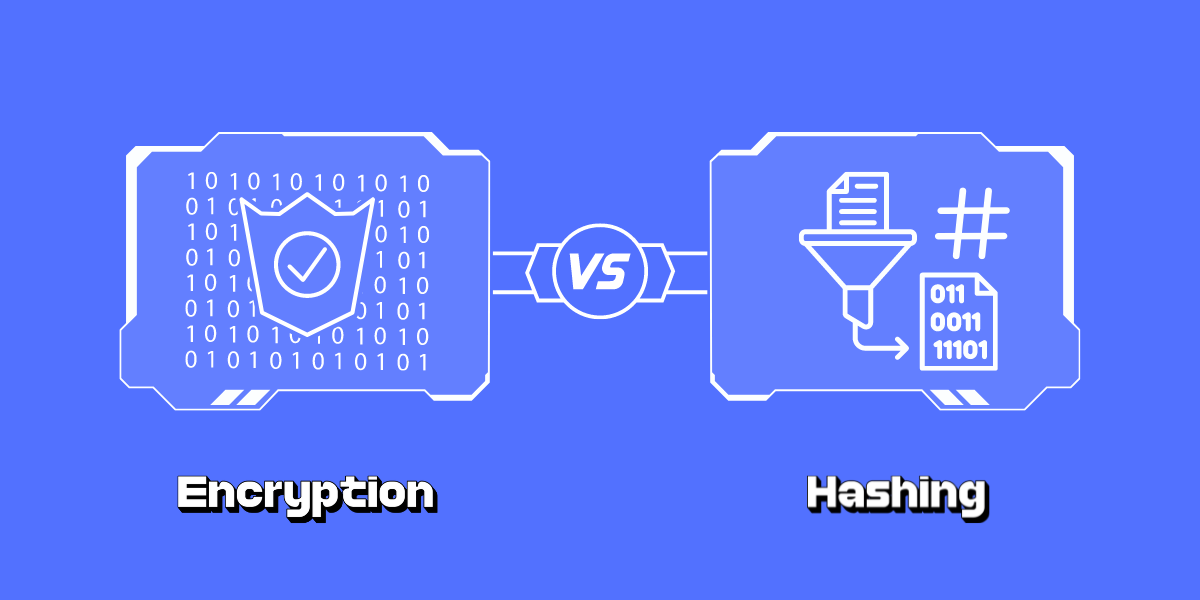
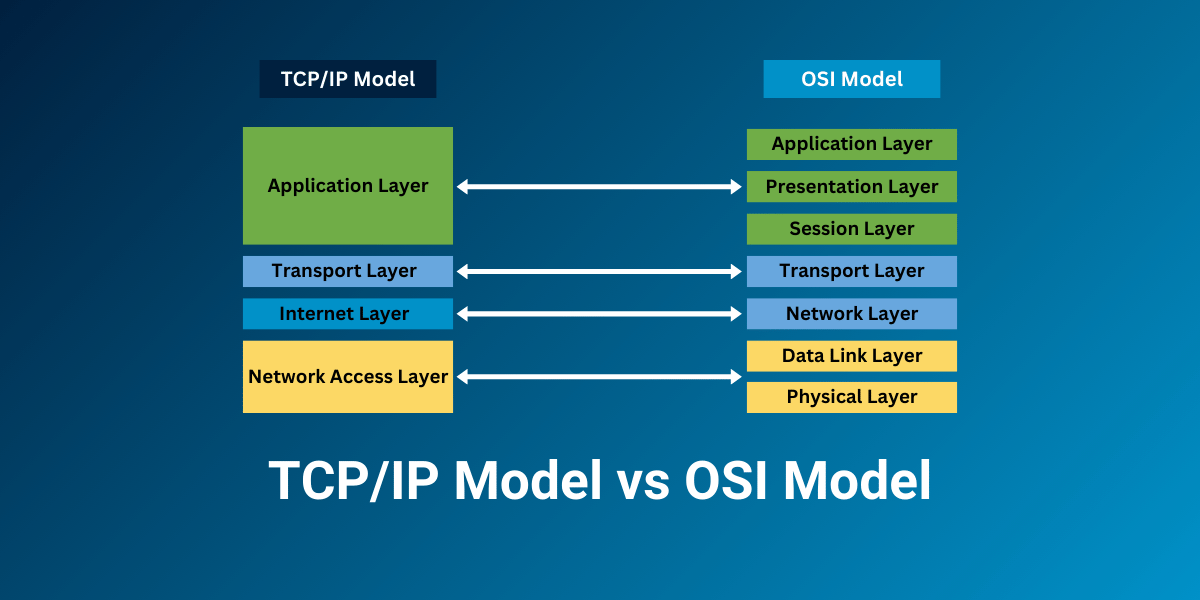
Symmetric vs Asymmetric Encryption: A Detailed Comparison Guide Encryption is a method of scrambling data so that only authorized parties can access it. There are two main techniques for encrypting data - symmetric encryption and asymmetric encryption. Both approaches...