A Basic Overview of VPN
Virtual Private Networks (VPNs) have become an essential tool in today’s digital landscape, providing users with secure and private internet access. As the demand for online privacy and security continues to grow, understanding the different types of VPNs is crucial. From remote access VPNs to site-to-site VPNs, each type offers unique features and capabilities to suit diverse user needs.
In this comprehensive guide, we will explore the various types of VPNs, their advantages, and how to choose the right one for your specific requirements. Whether you’re an individual seeking to protect your online activities or a business looking to secure your corporate network, delving into the different types of VPNs can help you make an informed decision.
Key Takeaways
- VPNs create an encrypted tunnel between your device and a server, hiding your traffic from prying eyes.
- The main protocols are PPTP, L2TP/IPsec, SSTP, IKEv2, OpenVPN, and WireGuard. Each has pros and cons.
- Key factors when choosing a VPN include encryption strength, speed, number of server locations, supported platforms, and pricing.
- Leading VPN types include remote access, site-to-site, mobile, router-based, and browser-based. Each fulfills different requirements.
VPN Protocols: How They Work
VPN protocols establish the rules and procedures for encrypting data and directing it between your device and the VPN server. Each protocol has technical specifications, security capabilities, and speed differences that affect performance.
- Point-to-Point Tunneling Protocol (PPTP)
- Layer 2 Tunneling Protocol (L2TP/IPsec)
- Secure Socket Tunneling Protocol (SSTP)
- Internet Key Exchange v2 (IKEv2)
- OpenVPN
- WireGuard
Point-to-Point Tunneling Protocol (PPTP)
One of the oldest and least secure protocols, PPTP is still defaulted on some operating systems. PPTP uses a TCP connection and general PKI encryption to encapsulate and transmit data between two hosts over the internet.
Pros: Ubiquitous support across platforms, fast connection speeds
Cons: Weak 128-bit encryption, security vulnerabilities
Layer 2 Tunneling Protocol (L2TP/IPsec)
L2TP does not provide encryption itself – it relies on IPsec to secure data. Combined as L2TP/IPsec, the double tunnel provides strong end-to-end security and integrity checking via “two layers” of protocols working together.
Pros: Strong 256-bit AES encryption, widely supported
Cons: Slower speeds than PPTP
Secure Socket Tunneling Protocol (SSTP)
SSTP transmits packets over port 443, making it appear indistinguishable from regular HTTPS traffic. Provides robust 256-bit encryption.
Pros: Evades firewall blocks, fast speeds
Cons: Only supported on Windows, not as secure as OpenVPN
Internet Key Exchange v2 (IKEv2)
IKEv2 uses IPsec encryption just like L2TP but builds on improved authentication and tunnel setup. Automated reconnect makes it great for mobile use.
Pros: Very secure, fast roaming between networks
Cons: Limited OS support; configuration can be complex
OpenVPN
OpenVPN uses OpenSSL libraries to provide strong AES-256-bit encryption over TCP or UDP transports. It is highly customizable across platforms.
Pros: Extremely secure, open source, reliable
Cons: More complex to set up than other protocols
WireGuard
This is a new approach using state-of-the-art cryptography, such as Curve25519 for key exchange and ChaCha20 for encryption. They are designed for high performance and ease of use.
Pros: Cutting-edge encryption, significantly faster than OpenVPN
Cons: Only recently launched, limited compatibility
VPN Protocol Comparison Table
|
Protocol |
Encryption |
Speed |
Compatibility |
Use Case |
|
PPTP |
Weak |
Fast |
Wide support |
Basic VPN needs |
|
L2TP/IPsec |
Strong |
Moderate |
Very common |
Reliable secure VPN |
|
SSTP |
Strong |
Fast |
Windows only |
Secure Windows VPN |
|
IKEv2 |
Very strong |
Fast |
Limited |
Mobile VPN |
|
OpenVPN |
Extremely strong |
Moderate |
Wide support |
High security VPN |
|
WireGuard |
Extremely strong |
Very fast |
Growing support |
Next-gen fast VPN |
Things to Know When Choosing a VPN
Beyond the protocol, several other factors determine the quality and capability of a VPN provider. Consider these closely when comparing options:
Encryption Strength
The strength of the cipher algorithm and key size applied by the VPN protocol impacts security. AES-256 bit is preferred, with SHA2 or RSA-4096 for handshake encryption.
Speed/Performance
VPNs introduce varying degrees of speed reduction. Try to find a provider who can deliver good speeds using your preferred protocol.
Number of Server Locations
More server options mean you’re more likely to find one nearby with less latency. Top providers have 1,000+ global server locations.
Bandwidth Limits
Check if your VPN provider imposes monthly data limits or speed caps that could constrain usage.
Supported Platforms
Make sure native apps are available for all your devices, such as Windows, Mac, iOS, Android, and routers.
Pricing
VPN plans range from free to $10-12 per month. Be wary of free VPNs selling your data. Aim for unlimited bandwidth without speed throttling.
Reliability & Support
A quality VPN should offer 99% uptime and responsive 24/7 customer support via live chat or phone. Try free trials to test reliability.
Types of VPN Configurations
Now that you understand VPN protocols and key factors that differentiate providers let’s examine the various VPN setups you can employ.
- Remote Access VPN
- Site-to-Site VPN
- Mobile VPN
- Router/WiFi Network VPN
- Browser/Proxy VPN
Remote Access VPN
A remote access VPN allows individual devices like laptops or smartphones to access a private network or resources securely. Access is authenticated via login credentials like a username/password. Traffic is encrypted between the remote device and the VPN server or gateway at the target network, which tunnels it through securely.
Remote access VPNs protect enterprise or home network access over public WiFi and allow remote employees to securely “telecommute” back to their office infrastructure. Popular implementations include Cisco AnyConnect and Microsoft DirectAccess.
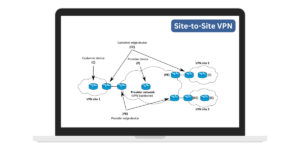
Site-to-Site VPN
As the name suggests, site-to-site VPNs connect entire physical office networks in different locations into one cohesive private network via encrypted tunnels through the public internet. This makes multi-site companies operate as though offices are directly connected, allowing seamless communication and collaboration.
Dedicated VPN routers are configured at each location to automate tunnel establishment with peer routers. Carriers often use Multiprotocol Label Switching (MPLS) VPNs to build out managed site-to-site networks. IPSec is another leading site-to-site protocol.
Mobile VPN
Designed specifically for mobiles and tablets, these VPNs use protocols like L2TP/IPsec or IKEv2 to maintain a persistent VPN that is “always on” as you roam between WiFi hotspots and cellular networks. This prevents privacy leaks across different mobile connections.
Leading examples include mobile apps from VPN providers like TunnelBear and Surfshark, which auto-connect in the background as you move around. This ensures your mobile activity is continually secured and private.
Router/WiFi Network VPN
Rather than manually configuring each device, you can enable a VPN for your entire home or office WiFi network by installing VPN server software on a router or dedicating a router for VPN termination.
Popular firmware options like DD-WRT let you set up a VPN gateway on a compatible router. You can also purchase a preconfigured router with VPN software from providers like ExpressVPN, which needs your login details to connect.
Browser/Proxy VPN
A proxy VPN provides VPN tunneling explicitly within your web browser to anonymize browsing data like IP address and DNS queries. This protects your browser traffic rather than device-wide.
Extensions like HolaVPN and SetupVPN add lightweight VPN functionality directly inside Chrome and Firefox for secure web surfing. However, other apps on your system do not route through the encrypted proxy.
VPN Use Cases: Work, Home, and On the Go
Now that you understand the landscape of VPN protocols and configuration modes let’s examine some common VPN applications:
Accessing Work Resources Remotely
Remote access VPNs let you securely “telecommute” back to your employer’s network from home to access intranet sites, internal databases, shared drives and documents, printers, and other resources as though physically in the office.
Securing Public WiFi Access
Connecting through a VPN when on public WiFi at coffee shops, hotels, and airports prevents snoops from intercepting your internet activity and hides your IP address.
Accessing Region-Restricted Content
Using a VPN tunnel server in another country allows you to bypass geographic content blocks and censorship to view overseas media sites like BBC iPlayer or Netflix with broader libraries.
Torrenting Safely and Privately
Downloading torrents through a VPN hides your IP address from peering users and copyright enforcers. This prevents malicious attacks or threats from being traced back to your real location or identity. VPN encryption secures the contents of your torrent traffic.
Protecting Mobile Connection Security
Mobile VPNs maintain persistent protection as you switch between WiFi hotspots and cellular data on phones and tablets. This prevents privacy leaks when moving between different untrusted networks.
Bypassing Internet Censorship
In countries with repressive internet controls and censorship, like China, a VPN tunnel to a server abroad allows citizens to circumvent blocks and access banned platforms like social media sites.
Safeguarding Internet Activity on Shared Computers
Using a browser VPN extension like SetupVPN when surfing the web from the public library or hotel business center computers prevents others from snooping through your browsing history and cached data after you log off.
Gaming Anonymously
Connecting to online games via VPN hides your IP address and physical location from other gamers, preventing DDoS attacks or other malicious actions from compromising your network security.
| Use Case | Recommended VPN Type |
| Remote work access | Remote access VPN |
| Public Wi-Fi security | Mobile VPN, browser proxy |
| Unblocking geo-restricted content | Remote access VPN |
| Safe torrenting | Remote access VPN |
| Mobile connection privacy | Mobile VPN |
| Bypass internet censorship | Remote access VPN |
| Shared/public computer privacy | Browser proxy VPN |
| Anonymous online gaming | Remote access VPN |
Final Thoughts
The world of VPNs is diverse and ever-evolving, offering a range of options to suit different online privacy and security needs. From traditional server-based VPNs to more advanced solutions like multi-hop and obfuscated VPNs, the choice depends on your specific requirements.
Whether you’re looking to bypass geo-restrictions, protect your data on public Wi-Fi, or maintain complete anonymity, understanding the different types of VPNs is crucial.
By carefully evaluating your needs and the features of each VPN type, you can make an informed decision and select the best solution to safeguard your online activities. Embrace the power of VPNs and enjoy a more secure and private internet experience.
Frequently Asked Questions About VPN Types
What is a VPN, and how does it work?
A VPN creates an encrypted tunnel between your device and a server run by the VPN provider. This protects your internet traffic by hiding your IP address and online activities from the sites you access. VPN encryption prevents outsiders from monitoring or modifying your data in transit.
Is a VPN worth it? What are the benefits?
Yes, a VPN provides many important privacy and security benefits, such as securing public WiFi hotspots, bypassing geo-blocks, hiding your IP address and location, and encrypting traffic. Leading VPNs are inexpensive and easy to use.
Does a VPN protect all traffic and apps on my device?
A device-level remote access VPN will tunnel all your system’s traffic through the encrypted connection, protecting all apps and processes. A browser VPN secures only web browsing traffic.
What should I look for in a quality VPN service?
Look for top protocols like OpenVPN or WireGuard, strong 256-bit AES encryption, a large server network, unlimited bandwidth without speed caps, easy-to-use apps for all your devices, and a no-logging policy to protect privacy.
Can using a VPN slow down my internet connection?
Yes, running traffic through a VPN introduces some speed loss, depending on the protocol. Overhead from encryption can impact connection speeds. Look for high-speed providers and connect to servers geographically close to you.
Are free VPNs safe to use?
Exercise caution with free VPNs. To turn a profit, they often exploit and sell user data, such as browsing habits. Paid VPNs like ExpressVPN offer better privacy protections and performance.
What is the difference between a VPN and a proxy?
A VPN encrypts and tunnels all traffic from your device to the VPN server. A proxy only routes web browser traffic through the proxy connection without broader device encryption.
Can a VPN protect me when torrenting?
Yes, using a VPN when torrenting is recommended to hide your IP address from peering users and copyright trolls. The VPN encryption will also secure the contents of your torrent traffic.
Are VPNs legal to use?
Yes, VPNs are legal in most regions. However, some repressive countries, like China, restrict VPN usage to censor content. Always check your local laws before using a VPN.
Can I access Netflix or other streaming sites with a VPN?
Many VPNs allow you to access region-locked streaming content on sites like Netflix and BBC iPlayer by routing your traffic through another country to bypass geographic blocks.

Jinu Arjun
 Verified Experienced Content Writer
Verified Experienced Content Writer
Jinu Arjun is an accomplished content writer with over 8+ years of experience in the industry. She currently works as a Content Writer at EncryptInsights.com, where she specializes in crafting engaging and informative content across a wide range of verticals, including Web Security, VPN, Cyber Security, and Technology.