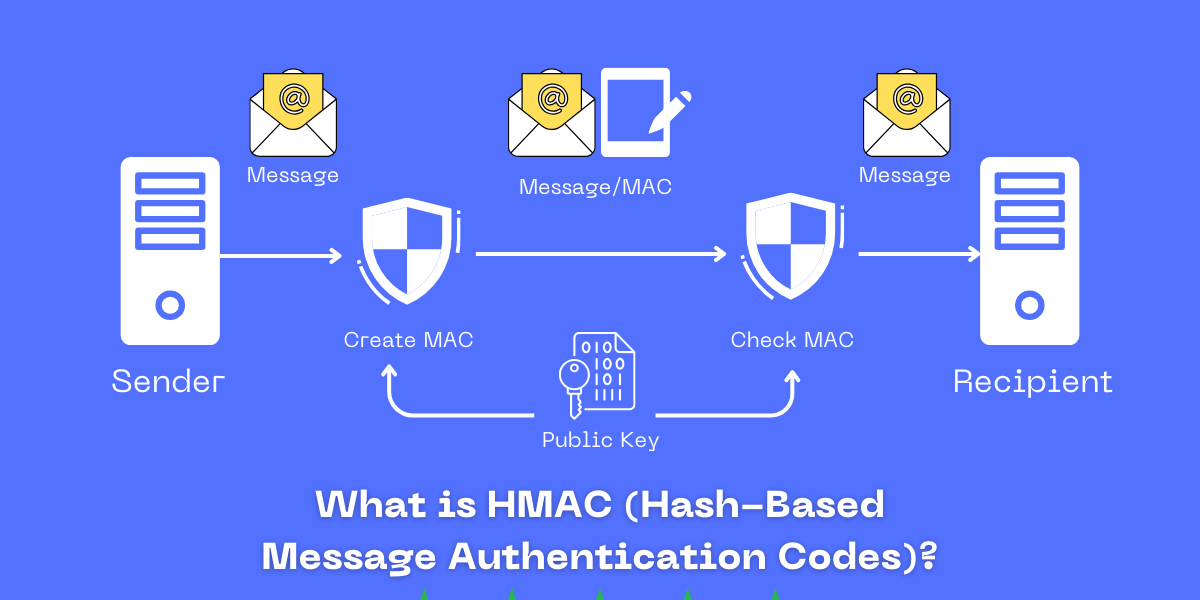
HMAC (Hash-Based Message Authentication Code) is a mechanism for calculating a message authentication code (MAC) involving a cryptographic hash function in combination with a secret key. It is used to verify a message's data integrity and authenticity simultaneously....