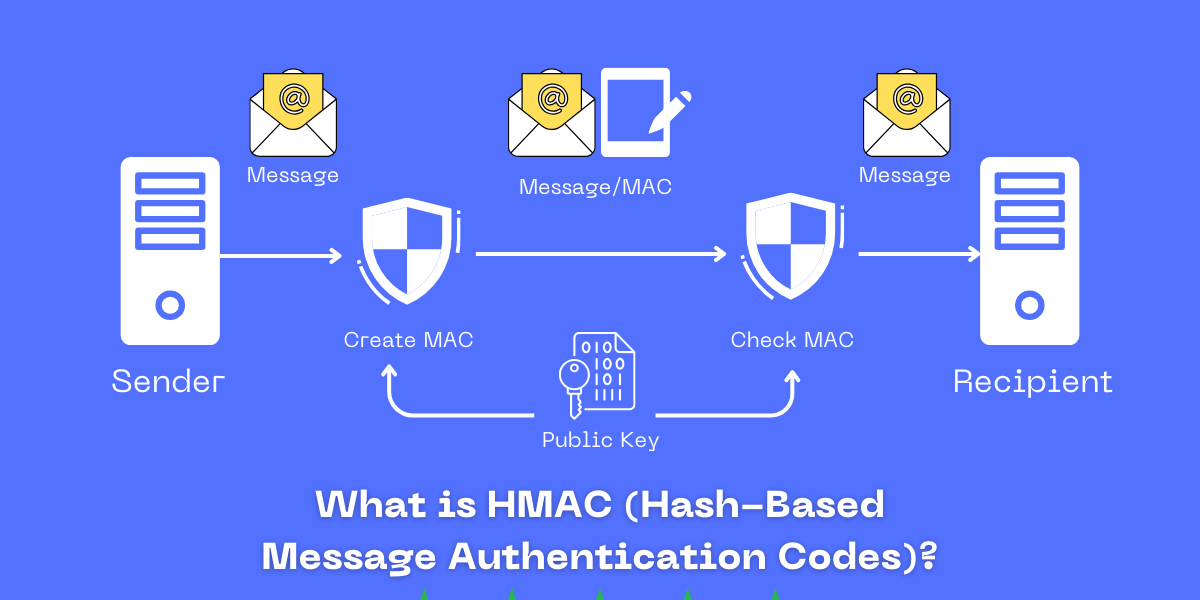
HMAC (Hash-Based Message Authentication Code) is a mechanism for calculating a message authentication code (MAC) involving a cryptographic hash function in combination with a secret key. It is used to verify a message's data integrity and authenticity simultaneously.
HMACs allow communicating parties to detect if a message has been altered, either intentionally or accidentally, during transmission. They can also verify that the message originated from the stated sender and was not tampered with in transit.
Key Takeaways:
- HMAC is a type of message authentication code (MAC) that uses a cryptographic hash function and a secret cryptographic key to produce a digital signature for a message.
- It verifies the integrity and authenticity of the message by allowing recipients to detect any changes to the content.
- HMAC offers protection against message forgery and tampering attacks. The secret key ensures that only authorized parties can generate or verify the HMAC.
- Common hash functions used in HMAC include MD5, SHA-1, SHA-2, and SHA-3. The strength of each function depends on the underlying hash algorithm.
- HMAC is widely implemented in applications like HTTPS, PGP, SSH, and IPsec to ensure secure data transmission.
- HMAC differs from digital signature algorithms because the secret key is required for both creating and validating the MAC tag. Digital signatures use public-key cryptography.
How HMAC Works
The HMAC algorithm involves concatenating the secret key with the message data, hashing the result, concatenating that hash value with the key again, and then hashing both again to produce the final MAC tag.
This tagging protects the integrity and authenticity of the message. The verification process repeats these steps to generate a new MAC tag from the received message and key. If the tags match, the message is authentic.
The components of HMAC include:
- Secret Cryptographic Key - A randomly generated key known only to the sender and receiver. Provides authentication, as only holders of the key can generate the MAC.
- Cryptographic Hash Function - A one-way function that maps data to a condensed representation called a hash value or digest. Popular choices include MD5, SHA-1, SHA-2, etc.
- Inner Hash - The hash of the secret key concatenated with the message data.
- Outer Hash - A second hash calculated over the concatenated result of the inner hash and the secret key.
- MAC Tag - The final output of the algorithm after outer hash, contains message digest. Verified against new MAC tag computed by the recipient.
The use of two separate hash operations with an intermediate step mixing in the secret key provides security protection. Even if the underlying hash function itself has collisions, the secret key ensures the MAC values are unique.
Why Use HMAC?
HMAC offers several advantages that make it suitable for a wide range of applications:
- Message Integrity - Any change to the message content will be detected, as it will cause the MAC tag verification to fail. This protects against accidental corruption or malicious tampering.
- Authenticity - Proof the message comes from the stated sender. The secret key means only authorized parties can generate valid MAC tags. Protects against spoofing or impersonation.
- Simpler Implementation - Only requires a hash function. Can use existing hash implementations like SHA-2 rather than complex encryption routines.
- Flexible Algorithm - Allows different hash functions to be plugged in. It can evolve by switching out for newer, more secure hashes.
- Better Security - Provides protections even if the hash function has theoretical collisions or weaknesses. Adds key randomness on top of the one-way hash operation.
- Performance - Hashing is faster than asymmetric "digital signature" algorithms. Allows efficient integrity checking on large data.
HMAC serves an integral role in securing communications and authenticating messages in systems where performance and interoperability are priorities.
HMAC Algorithms and Uses
HMAC can be implemented with any cryptographic hash function. Commonly used hash algorithms include:
- HMAC-MD5 offers relatively fast performance but is considered cryptographically broken by known collision attacks. It is not recommended for new applications but is still found in legacy systems.
- HMAC-SHA1 - Previously the default choice, it is now also deemed risky due to cryptanalysis advances. However, it is still adequate for non-security-critical applications needing a short MAC tag.
- HMAC-SHA2 - A family of robust hash functions - SHA-256, SHA-384, SHA-512. Offer collision resistance and high-security margins. A common choice for HMAC in new systems and protocols.
- HMAC-SHA3 - The latest secure hash algorithm standardized by NIST. It is not yet widely adopted, but offers future-proof security.
Some example applications and protocols using HMAC include:
- IPsec - Used in the IPsec protocol suite for authenticating network packets and ensuring the integrity of VPN tunnels and other services.
- TLS/SSL - Supported by TLS/SSL for HTTPS and other encrypted connections. Used in cipher suites for authentication of protocol messages.
- SSH - Used in SSH for remote command execution, file transfer, and other functions to detect any tampering or hijacking of the connection.
- PGP/GPG - Applied in PGP email encryption and GPG file encryption to ensure the integrity of encrypted messages and files.
- Cryptocurrencies - Utilized in Bitcoin and other blockchain platforms to authenticate transactions and protect consensus mechanisms.
- APIs - Commonly used in REST APIs and web services to sign and verify data payloads, API keys, and other transactional information.
How HMAC Differs from Digital Signatures
HMAC is sometimes confused with digital signature algorithms that also provide message authentication capabilities. However, some key differences include:
- Symmetric vs. Asymmetric - HMAC uses a shared secret key; digital signatures rely on public/private key pairs.
- Authentication Only - HMAC provides authenticity but not non-repudiation. Digital signatures give stronger assurances of origin.
- Performance - HMAC is faster at computing large amounts of data. Digital signatures are relatively slow.
- Key Security - HMAC secret keys must be kept secure by both parties. Public keys used in digital signatures can be openly shared.
- Cryptographic Primitives - HMAC uses hash functions only. Digital signatures require public-key cryptography.
- Use Cases - HMAC suits high-throughput message streams. Digital signatures are better for individual message security.
In essence, HMAC is lightweight and optimized for message integrity/authenticity. Digital signatures offer stronger assurances of origin and non-repudiation for sensitive transactions.
How Secure is HMAC?
The security of HMAC depends on several factors:
- Hash Function - A vulnerable hash exposes HMAC to attacks on the underlying construction. Needs strong collision resistance and one-way properties.
- Key Size - Longer key sizes make brute-force attacks more difficult. For modern applications, at least 128-bit keys are recommended.
- Key Management - Proper handling and protection of keys are essential. Key reuse weakens security by allowing more samples for cryptanalysis.
- Nonces and Rotation - Additional measures like nonces and periodic re-keying improve resilience against attacks over time with the same key.
- Tag Length - Longer MAC tag lengths reduce the odds of collisions. But lengthy tags add communication overhead.
- Implementation - Code quality, side-channel resistance, and other implementation concerns affect real-world robustness.
Like any cryptographic primitive, HMAC has some theoretical vulnerabilities if not implemented carefully with secure algorithms and keys. However, when applied properly, it remains a highly dependable technology for authentication.
HMAC Usage Best Practices
To leverage HMAC securely and effectively, consider these best practices:
- Use approved cryptographic hash functions, e.g., SHA-2 and SHA-3, and avoid deprecated ones like SHA-1.
- Generate secret keys with high entropy and randomness. Rotate keys periodically.
- Adhere to key size recommendations for the hash - at least 128-bit, 256-bit optimal.
- When possible, use full-length hash output sizes for the MAC tag.
- Add randomness via salting, nonces, timestamps, or other mechanisms for each message.
- Have defined policies for distributing and protecting HMAC keys. Avoid shared keys.
- Implement secure programming techniques and key management to prevent leakage.
- Keep software libraries, TLS/SSL suites, etc., updated to fix any published HMAC vulnerabilities.
- Consider using authenticated encryption rather than HMAC alone when cryptographic assurance requirements are high.
Following information security best practices around HMAC ensures strong protections for message integrity and authenticity in your applications.
Final Thoughts
HMAC is a versatile cryptographic algorithm that provides strong assurances of message authenticity and integrity through the use of hash functions and secret keys. It is widely adopted due to its performance, simplicity of implementation, and interoperability with existing hash standards. When implemented following best practices, HMAC can effectively protect communication networks and applications against attackers. The nested hash structure and optional use of random nonces also provide good resilience against cryptanalysis and brute force attacks. HMAC remains a vital and recommended tool for security architects and engineers needing to verify authenticity and prevent tampering with critical data.
Frequently Asked Questions About HMAC
What is the difference between an HMAC and a hash function?
The main difference is that HMAC includes a secret cryptographic key when computing the hash value over the data. Regular hash functions work only on the message content as input. The HMAC key provides authentication and prevents tampering since only holders of the key can generate the correct hash output.
Is HMAC considered a symmetric or asymmetric algorithm?
HMAC is considered a symmetric algorithm because it relies on a shared secret key known to both the sender and receiver. This contrasts with asymmetric "public key" algorithms like RSA or ECC that use key pairs.
Can you explain the purpose of the two nested hash operations in HMAC?
The inner hash protects the integrity of the message data. The outer hash mixes in the secret key to authenticate the resulting digest. This nesting technique provides security benefits even if the hash algorithm has theoretical weaknesses.
What are some common examples of using HMAC?
HMAC is widely used in network security protocols like IPsec, TLS, and SSH to ensure the integrity and authenticity of packets and connections. It is also used in cryptocurrency transactions, encrypted emails and files, secure APIs, and many other applications requiring message authentication.
Is HMAC susceptible to brute force attacks?
Like any algorithm relying on secret keys, HMAC could be vulnerable to brute forcing of the key if the key is not complex enough. This reinforces the need for high entropy keys of sufficient length. Longer MAC tags also increase the difficulty of collisions. Proper key management is critical.
How does HMAC provide authentication of a message?
The secret cryptographic key provides the authentication. Only someone with possession of the correct HMAC key can generate the same MAC tag from the message data. This proves to the receiver that the message came from the authorized sender and was not modified in transit.
Can HMAC be used with digital signature algorithms for added security?
Yes, HMAC can complement digital signatures in a security protocol. The signature provides strong assurances of authenticity and non-repudiation from the sender. Adding an HMAC allows for confidentiality and integrity verification of the message contents. The two techniques are complementary.
Is HMAC secure against replay attacks?
Basic HMAC alone does not prevent replay attacks. To prevent replays, the sender should include a nonce or unique value, like a timestamp or sequence number, with each message, which is then signed by the HMAC. The receiver discards duplicate messages with the same nonce and HMAC.
Does HMAC require synchronized time between sender and receiver?
No. HMAC does not rely on time synchronization between parties. Some applications may include timestamps in the data to prevent replays, but the algorithm itself does not mandate this. The security is based on the HMAC key.

Jinu Arjun
 Verified Experienced Content Writer
Verified Experienced Content Writer
Jinu Arjun is an accomplished content writer with over 8+ years of experience in the industry. She currently works as a Content Writer at EncryptInsights.com, where she specializes in crafting engaging and informative content across a wide range of verticals, including Web Security, VPN, Cyber Security, and Technology.