Public Key Infrastructure (PKI): Everything You Need to Know
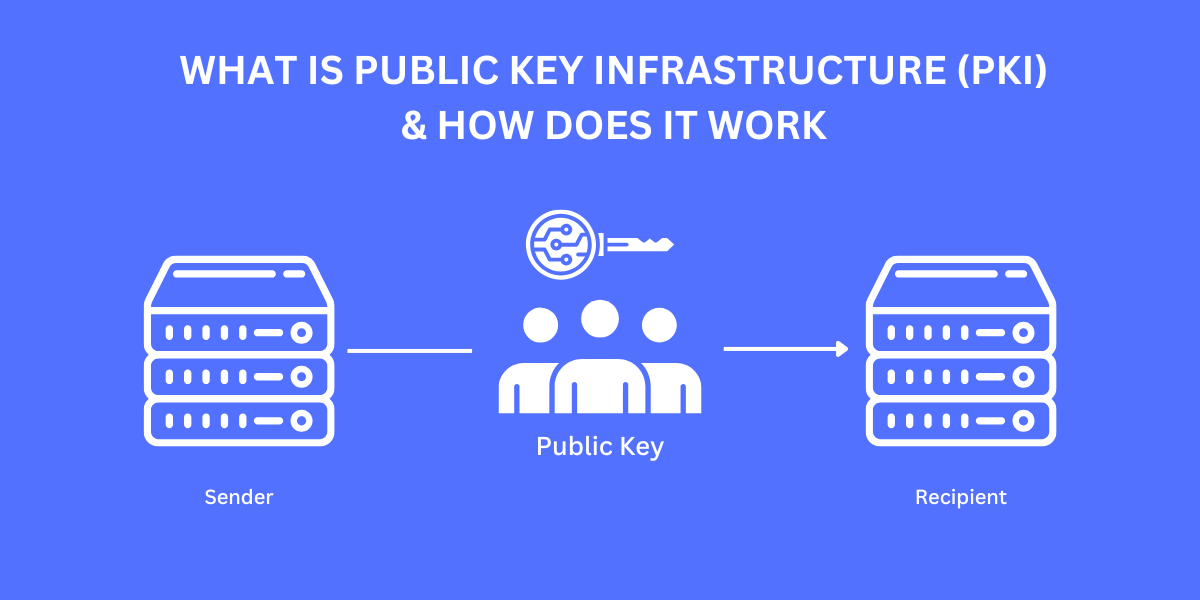
Public key infrastructure (PKI) is a system of digital certificates, certificate authorities, and other registration authorities that verify and authenticate the validity of each party involved in an electronic transaction. PKI establishes trust by providing a mechanism to confirm that the public cryptographic keys involved actually belong to the entities claiming ownership.
Key Takeaways:
- PKI enables the secure electronic transfer of information for activities like e-commerce, internet banking, and confidential email by using public key cryptography.
- It establishes a trust framework by binding public keys with respective user identities through the use of public key certificates.
- PKI involves an ecosystem of certification authorities, registration authorities, certificates, and policies for managing, issuing, and revoking them.
- The core components of PKI are digital certificates, public keys, private keys, and certificate authorities that issue and revoke certificates.
- PKI provides integrity, confidentiality, and authenticity for electronic transactions through the use of public key encryption, digital signatures, and hashes.
- Common uses of PKI include SSL/TLS certificates for websites, code signing certificates, S/MIME email certificates, and authentication of devices and users.
- While PKI helps solve the key distribution and identity problems in cryptography, compromised CAs or certificates can enable cyberattacks to bypass PKI security.
The Need for Public Key Infrastructure
The internet and digital information systems have enabled fast, easy global transfer of data and value online. E-commerce websites, internet banking systems, and email are some examples that allow people across geographies to transact and communicate online.
However, these capabilities also increase the risk of security threats like fraud, data theft, and espionage. Sensitive information like credit card details, account passwords, and confidential data need to be protected when transferred online.
This is where public key infrastructure comes in. PKI provides the basis for secure communications in digital systems by enabling authentication, integrity, and confidentiality services.
Before diving into how PKI works, it helps to understand the cryptography concepts on which PKI is built.
Public Key Cryptography
Conventional cryptography relies on a single key for encrypting and decrypting data. The sender uses this key to transform plaintext into ciphertext, and the receiver uses the same key to reverse the encryption.
The problem is securely delivering the key to communicating parties before transferring information. Anyone intercepting the key can decrypt the data.
Public key cryptography solves this problem by using a pair of asymmetric keys - a public key and a private key. As the names suggest, the public key can be openly shared while the private key remains a secret.
A message encrypted by a public key can only be decrypted by the corresponding private key. This allows anyone to encrypt messages using the public key, but only the holder of the private key can decrypt it.
How Public Key Infrastructure Works
Public key infrastructure utilizes public key cryptography to provide key security services:
- Authentication - Confirming the identity of entities like user, device, or website
- Integrity - Detecting unauthorized alteration of data
- Confidentiality - Protecting against unauthorized access to data
- Non-Repudiation - Ensuring the entity cannot deny actions or transactions
PKI establishes and propagates trust by issuing, distributing, and revoking digital certificates. A digital certificate binds an entity's identity to its public key using a digital signature from a trusted certificate authority (CA).
Core Components of a PKI System
Digital Certificates
A digital certificate is an electronic document that uses a digital signature to bind a public key with an identity. A certificate authority issues it and verifies the ownership of a public key by the named subject of the certificate.
The most common standard for certificates is X.509, which defines the format for public key certificates. X.509 certificates include identifying information like:
- Subject - Identity like a person, organization, or device being certified
- Issuer - The CA that issued the certificate
- Public Key - The public key being certified
- Validity Period - Start and end dates for certificate validity
- Signature Algorithm - Algorithm used by CA to sign the certificate
- Signature - CA's signature to authenticate the certificate
Certificates enable the public verification and authentication of keys before sensitive information is exchanged.
Public and Private Keys
The public and private keys used in PKI are mathematically related. However, whereas the public key can be openly shared, the private key must be kept secure. Here's how they work together:
- The certificate subject keeps the private key secret. This key is used to sign data or decrypt ciphertexts digitally.
- The corresponding public key is embedded in the certificate and can be freely distributed. Others use it to verify signatures or encrypt messages to the subject.
By making the public key easily available through a certificate while restricting access to the private key, PKI enables secure key establishment prior to communication or transactions.
Certificate Authorities
A certificate authority (CA) issues and manages X.509 certificates and certificate revocation lists. CAs are responsible for:
- Verifying identity and credentials provided in certificate requests
- Issuing certificates binding identities to public keys
- Signing certificates to vouch for their validity
- Publishing issued certificates and certificate revocation lists
- Revoking certificates is no longer considered valid
CAs form trust anchors that stakeholders can depend on to issue legitimate certificates. A CA's certificate is directly trusted by the entities using the certificates it issues.
Major types of CAs include root CAs, intermediate CAs, and issuing CAs. They can establish hierarchies and chains of trust.
Registration Authorities
Registration authorities (RAs) operate under CAs to identify and authenticate certificate applicants. An RA verifies applicants' identities before submitting certificate requests to the CA for signing.
Large organizations often operate their RAs and integrate them with the CA to manage certificates for their users, devices, or systems.
Certificate Policies and Practice Statements
Certificate policies define the norms and criteria for issuing, using, and managing certificates within a PKI system. They help establish trust by setting standards that CAs and subscribers must adhere to.
Related to these are certification practice statements - detailed descriptions of the specific practices employed by a CA when issuing certificates. These provide operational details on certificate issuance, verification steps, security controls, and more.
Digital Signatures and Hashes In PKI
Two other fundamental components used by PKI systems are:
Digital Signatures
A digital signature is a mathematical scheme used to validate the authenticity and integrity of digital messages or documents.
It is generated by creating a hash of the message contents, encrypting this hash value with the signer's private key, and appending it to the message.
The signature can then be validated by the receiver using the signer's public key to verify that the message has not been tampered with since signing. This also confirms the message originated from the expected sender.
Hashes
A cryptographic hash function generates a condensed fixed-length output (hash value or digest) from an input message of any size. It is designed as a one-way function, and it is infeasible to reverse it to retrieve the original message.
Even a minor change in the message results in a completely different digest, which helps detect unauthorized changes. Hashes provide integrity protection to signed messages and certificates in PKI systems.
Common Uses of Public Key Infrastructure
By providing a standardized trust framework for identities and public keys, PKI enables several essential cryptographic processes. Some common PKI applications are:
- SSL/TLS certificates - Enable encrypted HTTPS websites by establishing server identity.
- Code signing certificates - Sign software binaries to verify publisher identity & integrity.
- Email signatures & encryption - Standards like S/MIME allow signing/encrypting email using PKI.
- Document signing - Apply digital signatures to documents like PDFs and Word files.
- Smartcard authentication - Employee ID passports use PKI to confirm identities.
- IoT device identity - Authenticate and encrypt communication between IoT devices.
Overall, PKI provides the backbone for trust establishment in many cybersecurity processes today.
Limitations of PKI Security
While PKI enables greater security for digital transactions and data transfers, it needs to be more foolproof. Some key limitations include:
- Compromised CAs can issue fraudulent certificates that are trusted within the PKI ecosystem.
- Weak private key management by end entities can lead to compromise of keys and digital identities.
- Improper validation of certificates by relying parties makes the system vulnerable to forged certificates.
- Certificate revocation mechanisms are sometimes slow to update, enabling the use of revoked certificates.
- Complexity in operating PKI systems leads to misconfigurations that undermine security controls.
To maximize PKI security, organizations must follow best practices for the issuance, distribution, renewal, and revocation of certificates. Users and relying parties also need to validate certificates properly.
Final Thoughts
Public key infrastructure establishes trust between unknown parties on the internet by issuing digital certificates tying identities to public keys. PKI enables the use of encryption, digital signatures, and cryptographic hashes to provide authenticity, integrity, and confidentiality for electronic transactions.
While technical vulnerabilities exist, PKI remains fundamental to security controls like HTTPS, code signing, document signing, and email encryption. Careful implementation and management of PKI components is essential to utilize its benefits while minimizing risks.
Frequently Asked Questions
What is PKI used for?
PKI enables secure communications and transactions in digital environments. Main PKI applications include SSL/TLS certificates for websites, signed software installers, encrypted and signed emails, and certificate-based authentication of users, devices, and servers.
What are the components of a PKI system?
The core components of a PKI system are digital certificates, public/private key pairs, certificate authorities that issue and revoke certificates, and registration authorities that authenticate certificate requests. Hashes and digital signatures are also used to protect integrity.
What does a certificate authority do?
A certificate authority is responsible for verifying entity identities, issuing digital certificates binding their identity to a public key, signing certificates to attest their validity, publishing certificate status information like revocation lists, and revoking certificates when required.
What is a public key used for in PKI?
The public key in a PKI system is contained within the digital certificate and freely shared. It allows entities who have the certificate to encrypt messages to the subject or verify digital signatures created by the subject's corresponding private key.
What is a private key used for in PKI?
The private key in PKI is kept secret by the certificate subject. It is used to decrypt messages that were encrypted using the corresponding public key or digitally sign messages and data to prove authenticity.
How are digital certificates used for security?
Digital certificates allow for authenticating identities and exchanging public keys securely before communication or transactions. Certificates are validated against CA certificate chains to prove validity. This prevents man-in-the-middle attacks through forged keys.
How does PKI enable HTTPS security?
Browsers and servers authenticate each other in HTTPS using PKI certificates issued and signed by trusted CAs. This allows for the establishment of secure TLS-encrypted channels using the public keys in the certificates, providing data security and site authenticity.
What are the vulnerabilities of PKI systems?
Vulnerabilities include weak private key management; CA compromises enabling fraudulent certificates, flaws in certificate validation, slow revocation of compromised certificates, and improper PKI implementation leading to bypass of controls.
How does PKI provide non-repudiation?
By requiring private keys for the digital signing of transactions and data, PKI ensures senders cannot repudiate or deny those transactions later, providing accountability and non-repudiation. The signature can be mathematically verified against the public key certificate.

Jinu Arjun
 Verified Experienced Content Writer
Verified Experienced Content Writer
Jinu Arjun is an accomplished content writer with over 8+ years of experience in the industry. She currently works as a Content Writer at EncryptInsights.com, where she specializes in crafting engaging and informative content across a wide range of verticals, including Web Security, VPN, Cyber Security, and Technology.