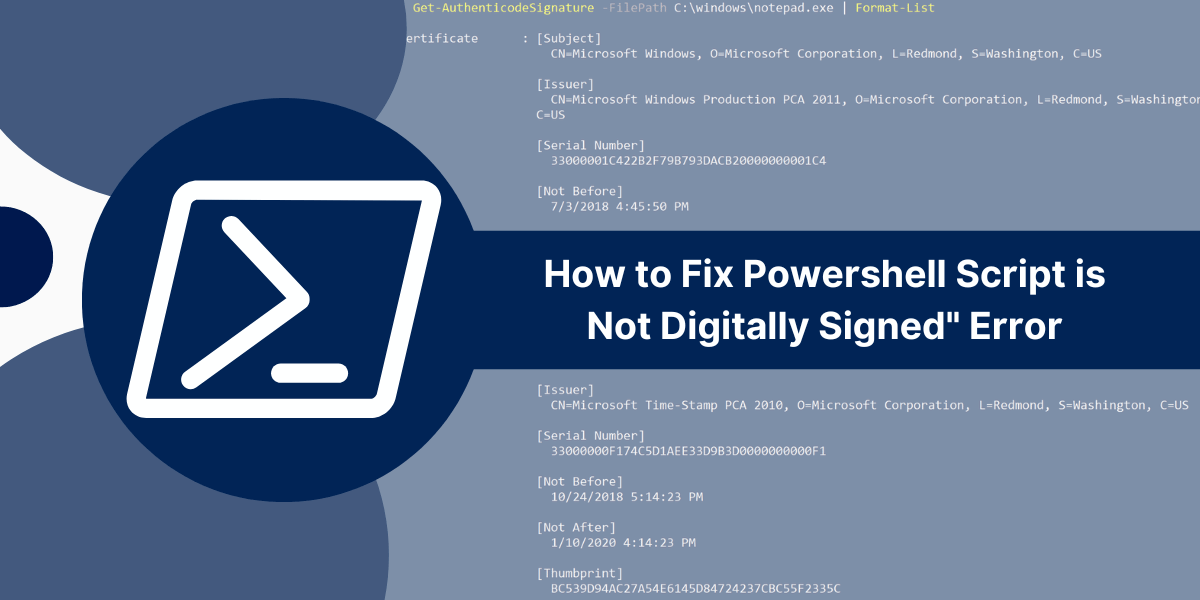
What Does "Powershell Script is Not Digitally Signed" Error Mean? Dealing with the "Powershell script is not digitally signed" error message can be frustrating. This error pops up when running unsigned PowerShell scripts and blocks the execution for security reasons....