LDAP: Definition, Benefits, Use Cases & How It Works
In today's networked world, directories containing information about users, devices, applications, and other resources are essential for managing access, security, and more across an organization. LDAP provides a standardized way for diverse applications to access and manage directory information services hosted on a server from anywhere on the network.
LDAP was originally developed in the early 1990s at the University of Michigan as a front-end to directory systems like X.500. It was designed to be lightweight and run over TCP/IP instead of the full OSI networking stack used by X.500. This allowed LDAP to become broadly adopted across the Internet.
Over time, LDAP has evolved to include new features for access control, extensions for special purposes, and standards for working with modern technologies and architectures. LDAP v3, published in 1997, is the current widely adopted version of the LDAP protocol.
Major directory services, including Active Directory, Apache Directory, OpenLDAP, and Oracle Internet Directory, rely on the LDAP protocol for user and application access. All major operating systems support LDAP, and it is a key technology enabling identity and access management in enterprises and organizations globally.
Key Takeaways:
- LDAP is an open, cross-platform protocol used for accessing distributed directory services. It allows applications to access and manage LDAP directory tree data in a standardized way.
- LDAP organizes information in a hierarchical structure as directory entries that reflect the organizational structure, people, devices, and more. Each entry has a unique Distinguished Name (DN).
- LDAP uses a client-server model. The LDAP server manages the directory data and responds to requests from LDAP clients.
- Common LDAP operations include searching, adding/modifying/deleting entries, modifying DN, comparing entries, and more. LDAP is optimized for read performance.
- LDAP can be used for authentication, authorization, and accounting (AAA) functions, storing user account information centrally rather than on individual systems.
- LDAP is commonly used in enterprise environments for centralized authentication, distributed information management, and the enforcement of security policies. Major directory services like Active Directory use LDAP.
- Key benefits of LDAP include simplified management, centralized access control, easier integration between systems, and more. Challenges include complexity, lack of built-in security, and insufficient performance monitoring.
What is LDAP?
The Lightweight Directory Access Protocol (LDAP) is a protocol used to access and maintain directory information services over an Internet Protocol (IP) network. LDAP is an open, vendor-neutral protocol that runs over TCP/IP and allows users to access distributed directory services to retrieve information about users, devices, networks, services, and applications.
How LDAP Works
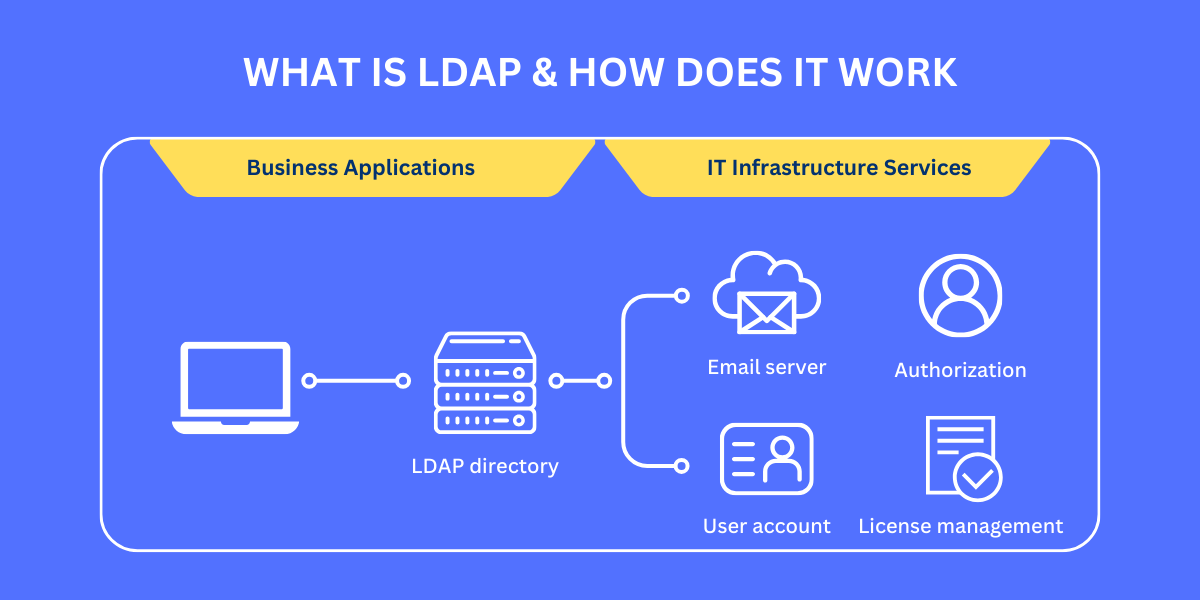
LDAP is designed as a client-server protocol that runs over TCP/IP. The LDAP server manages the directory data and handles requests from LDAP clients to access and modify that data.
LDAP Directory Structure
The information in an LDAP directory is organized hierarchically in a tree-like structure consisting of the following components:
- Entry: A single unit or node in the LDAP directory tree containing information about an object, such as a user, group, device, or resource. Represented by a Distinguished Name (DN).
- Attribute: Information elements associated with each directory entry, like name, address, and phone number. Each attribute has assigned syntax controlling the type of values it can hold.
- Object Classes: Templates that define what attributes an entry can contain based on its purpose. User, group, and organization are common object classes.
- LDAP Schema: This schema defines the rules for object classes and attributes in a given LDAP directory. All servers and clients follow the same schema.
- Naming Contexts: Logical groupings of related entries, allowing the Directory to be partitioned.
This hierarchical structure reflects real-world organizational arrangements and allows efficient searches to locate specific information. The path to each entry's position in the hierarchy is defined by its DN, providing a unique identifier similar to a file path.
LDAP Operations
Clients interact with the LDAP server using operations like:
- Search - Retrieve specific entries or search for entries matching criteria.
- Compare - Check if an entry contains a given attribute value.
- Add - Create a new entry.
- Delete - Remove an existing entry.
- Modify - Change the value of an entry's attributes.
- Modify DN - Move or rename an entry.
- Bind - Authenticate a user to permit access to directory operations.
- Unbind - Disconnect the client from the LDAP server when done.
LDAP is optimized for frequent read operations in high-volume directories. Writes are less frequent compared to directory lookups and searches.
LDAP Security
Some key mechanisms used to secure LDAP include:
- Transport Layer Security (TLS): Encrypts communication between clients and LDAP server.
- Simple Authentication and Security Layer (SASL): Provides authentication and data security services.
- Access Control Lists (ACLs): Allow administrators to set policies restricting what users or applications can access.
- LDAP over SSL (ldaps): Provides encryption by tunneling LDAP over SSL/TLS connections.
Client Communication
LDAP clients connect to the LDAP server using TCP and communicate using the LDAP protocol. Clients construct LDAP operations containing requests and send them to the server.
The server processes the request, performs necessary actions on directory data, and returns a response. The client then uses the response to take application-specific actions.
Common LDAP client libraries include JNDI in Java and Active Directory Service Interfaces (ADSI) in .NET. LDAP command line tools like ldapsearch help administrators interact directly with LDAP servers.
Use Cases for LDAP
LDAP is a mature, versatile technology that can serve a variety of roles in modern IT environments:
Directory Services
LDAP's basic function is to provide centralized directory services. LDAP servers act as a single source of truth for information on users, groups, hosts, applications, and other objects shared across an organization's infrastructure.
Authentication and Access Control
LDAP is commonly used to authenticate user credentials for access to systems and applications across an enterprise. Centralized LDAP-based authentication replaces individual application user accounts.
Single Sign-On (SSO)
LDAP can enable single sign-on by allowing users to log in once and be automatically authenticated when accessing connected systems. SSO eliminates multiple passwords and improves security.
Identity Management
Using LDAP, user accounts, access rights, passwords, groups, and other identity-related information can be managed in one place for simplicity and consistency.
Domain Controllers
Active Directory domain controllers use LDAP to handle communication between AD components, such as managing user accounts, logon processes, policies, and replication.
Dynamic Directories
LDAP's searching capabilities allow directories to be used dynamically for real-time lookups. For example, LDAP can deliver information to users based on context.
Network Devices
Device-specific information, such as hostnames, IP addresses, and configuration settings, can be stored in LDAP directories for centralized management.
Mail/Collaboration Services
LDAP can provide authentication for mailing and collaboration platforms. It can also manage user directory details like contacts and distribution lists.
Key Benefits of LDAP
LDAP offers significant advantages for accessing and maintaining directory services:
- Standard protocol - Open, vendor-neutral protocol supported across many platforms and languages. Replaced proprietary protocols.
- Simplified management - Centralized directories simplify managing user accounts and resources vs. individual servers and databases.
- Flexibility - LDAP schemas and object classes can be customized for specific use case requirements.
- Integration - LDAP allows easier integration between directory-enabled systems and applications. Enables single sign-on.
- Consolidated directories - Multiple directories, like siloed HR databases, can be consolidated into unified LDAP directories.
- Improved security - Access control lists and encryption help securely expose directories over networks.
- High availability - LDAP servers can be clustered to eliminate single point-of-failure.
- Scalability - Mature implementations scale to tens of millions of entries and thousands of concurrent users.
Challenges with LDAP
However, LDAP also comes with certain drawbacks that must be considered:
- Complexity - Requires expertise to properly design schema, build efficient search filters, and secure and optimize performance.
- Access control limitations - Finer-grained role-based access control (RBAC) requires extensions. Native access controls are entry-based.
- Limited monitoring - Most LDAP servers lack comprehensive performance monitoring and analytics.
- No built-in redundancy - High availability requires additional components like load balancers.
- Vulnerable connections - Encryption and certificate management are not inherently built into the protocol.
- Bulk import challenges - Bulk loading large directories can be problematic and require workarounds.
LDAP vs. Other Directory Services
LDAP is one of several protocols that can provide directory services and has some key differences from alternatives:
LDAP vs. X.500
- LDAP is lightweight and runs over TCP/IP, while X.500 uses the full OSI stack, which has more overhead. This makes LDAP better suited for Internet use.
- X.500 uses a global directory model, while LDAP can segment directories. LDAP has no limit on the number of entries.
- X.500 requires full replicas, but LDAP supports partial replicas for improved scalability.
- LDAP supports anonymous access, which X.500 does not allow.
LDAP vs. NIS
- LDAP allows a hierarchical tree-based structure, while NIS uses flat namespaces, making it less scalable.
- LDAP has more fine-grained access control vs NIS host-based access control.
- LDAP is an open standard, while NIS is proprietary to Sun/Oracle.
- LDAP supports SSL/TLS encryption, while NIS does not encrypt by default.
LDAP vs Active Directory
- Active Directory is Microsoft's proprietary directory service that heavily leverages LDAP standards for querying and managing directory data.
- Active Directory adds features like Group Policy, DFS replication, and advanced security policies on top of LDAP foundations.
- Active Directory requires Microsoft Windows servers, while LDAP can run on many operating systems.
Getting Started with LDAP
Here are some recommendations for organizations new to implementing LDAP solutions:
- Clearly identify use cases and directory information requirements upfront. This drives design choices.
- Keep the schema and design simple initially, and then expand as needed. Avoid overly complex schemas.
- Use LDAP monitoring tools and benchmarks to baseline and optimize performance. Test with realistic data volumes and usage.
- Validate security controls and access policies before rolling them out to production. Perform penetration testing.
- Implement LDAP redundancy through server clustering to eliminate single points of failure.
- Gradually shift legacy application accounts over to LDAP rather than all at once. Phase rollouts.
- Train administrators and support teams on managing, securing, and troubleshooting LDAP environments.
- Document LDAP architecture, operational procedures, security policies, and other key information. Keep updated.
Final Thoughts
LDAP has cemented its place as a widely used protocol for accessing directory services across platforms, languages, and technologies. It enables centralized, secure access to user accounts, network resources, and other identity and policy information critical for managing modern IT environments and infrastructure.
While deploying LDAP offers compelling advantages, it also comes with its challenges that must be addressed through careful design, capacity planning, and administration. For organizations looking to derive the benefits of unified access control, single sign-on, simplified identity management, and more, investing in expertise with LDAP solutions can provide a foundation for present and future needs.
Frequently Asked Questions About LDAP
Here are some common questions about LDAP and its implementation:
What are the key components of LDAP?
The main components of LDAP are:
- The LDAP server hosts the directory data.
- LDAP clients make requests to the server.
- The LDAP protocol defines the communication between them.
LDAP also includes schemas governing directory objects and attributes.
What types of information can be stored in an LDAP directory?
Typical LDAP directory content includes user identities such as login IDs, contact details, group memberships, hostnames, IP addresses, digital certificates, application settings, and any other data that can be represented as directory object attributes.
How does LDAP compare to a database?
While both can store information, LDAP is optimized for fast reads with infrequent updates, suited for directory lookups. Databases allow more complex querying and analysis unneeded in LDAP and support more robust transaction mechanisms.
What are common ways to secure LDAP?
Encrypting LDAP connections using SSL/TLS, restricting access with ACLs, using password policies, disabling insecure features like anonymous binds, and proper infrastructure security controls like firewalls help secure LDAP servers.
Can LDAP integrate with Active Directory?
Yes, LDAP can be used to access and manage information stored in Active Directory since AD is built on LDAP standards. AD also includes security extensions like Kerberos authentication. LDAP can complement AD deployments.
What languages support LDAP programming?
Many languages have LDAP client libraries including Java, .NET/C#, Perl, Python, Ruby, PHP and C/C++. Code can directly interface with an LDAP server using language-specific APIs.
How does LDAP scale compare to other directory services?
If properly optimized, LDAP scales very well compared to alternatives. Production deployments support tens of millions of entries and thousands of simultaneous user connections by using replication and load balancing.
Can LDAP be used for purposes other than authentication?
Yes. While authentication is a very common use case, LDAP also excels at distributed information management, enforcing access controls, powering directory-enabled applications via LDAP lookups, and more.
Is LDAP only used in private internal networks?
No. While LDAP is very common internally in organizations, it can also be used for public-facing directories. For example, LDAP enables directory services to be exposed on the Internet, like corporate contact websites.
What is an LDAPv3 server?
An LDAP version 3 server implements the LDAPv3 protocol defined in RFC 4510. LDAPv3 added several enhancements over LDAPv2, such as TLS support, dereferencing aliases, managing schemas, and SASL for advanced authentication.

Jinu Arjun
 Verified Experienced Content Writer
Verified Experienced Content Writer
Jinu Arjun is an accomplished content writer with over 8+ years of experience in the industry. She currently works as a Content Writer at EncryptInsights.com, where she specializes in crafting engaging and informative content across a wide range of verticals, including Web Security, VPN, Cyber Security, and Technology.