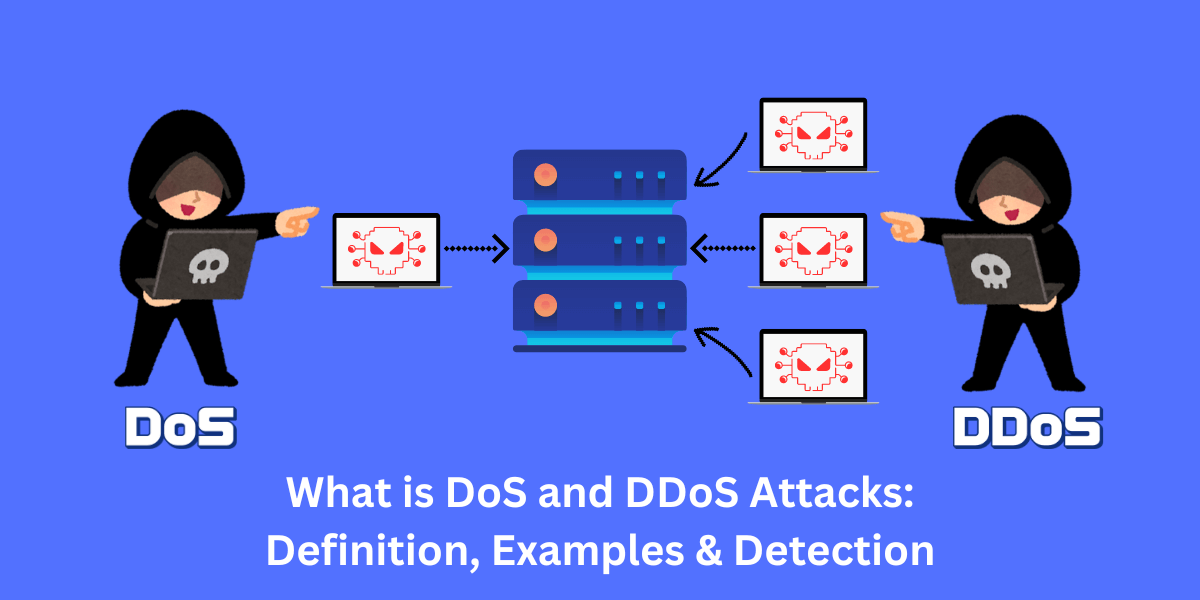
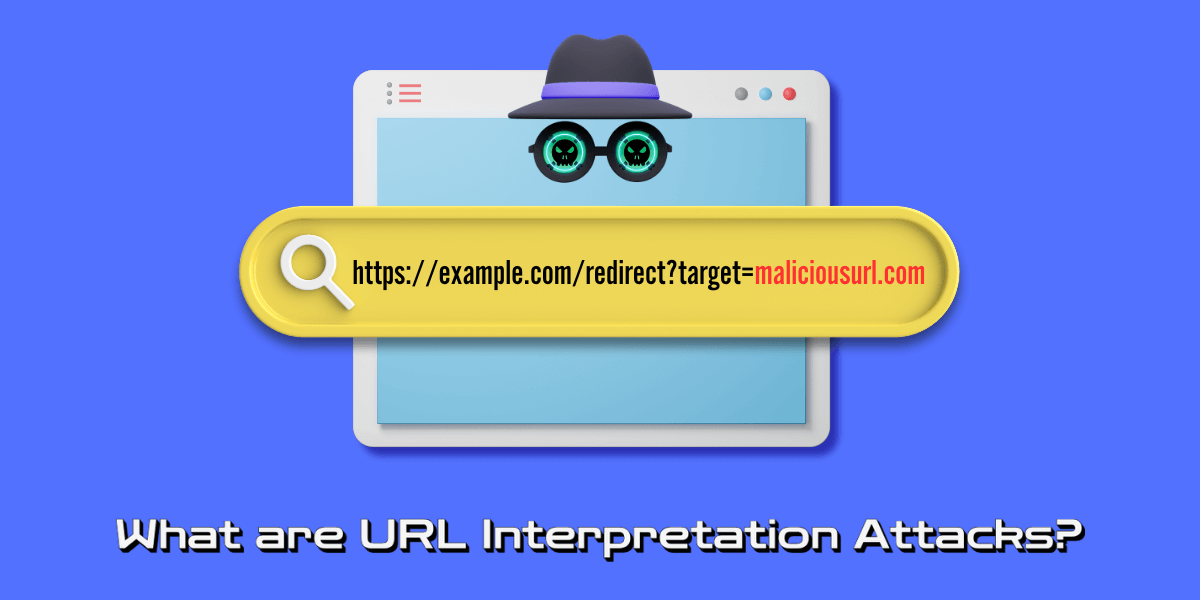
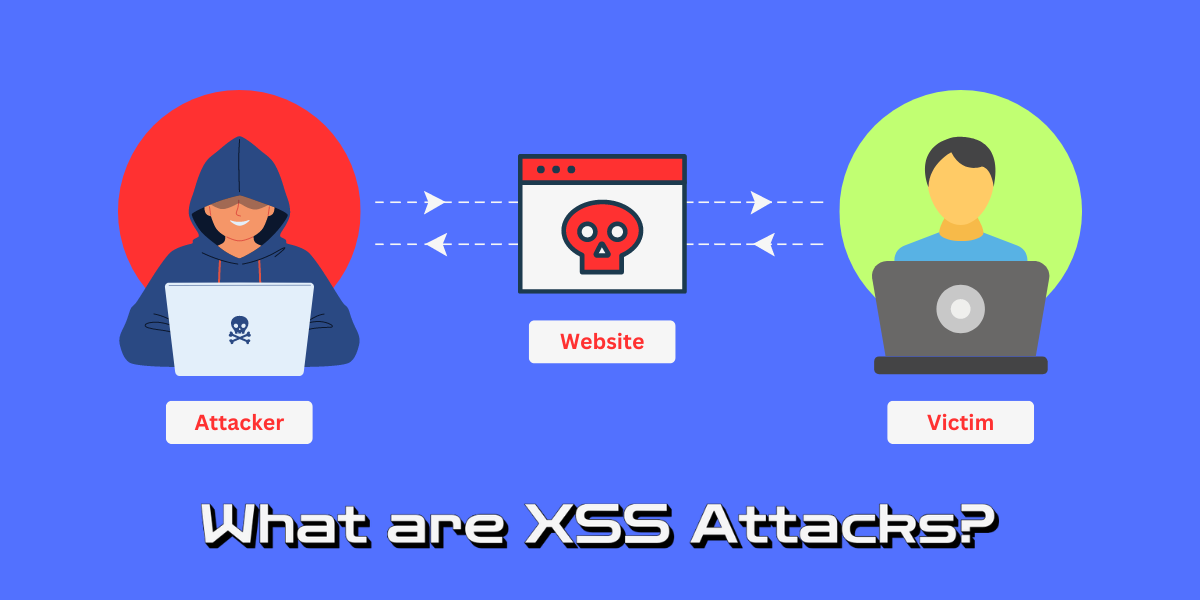
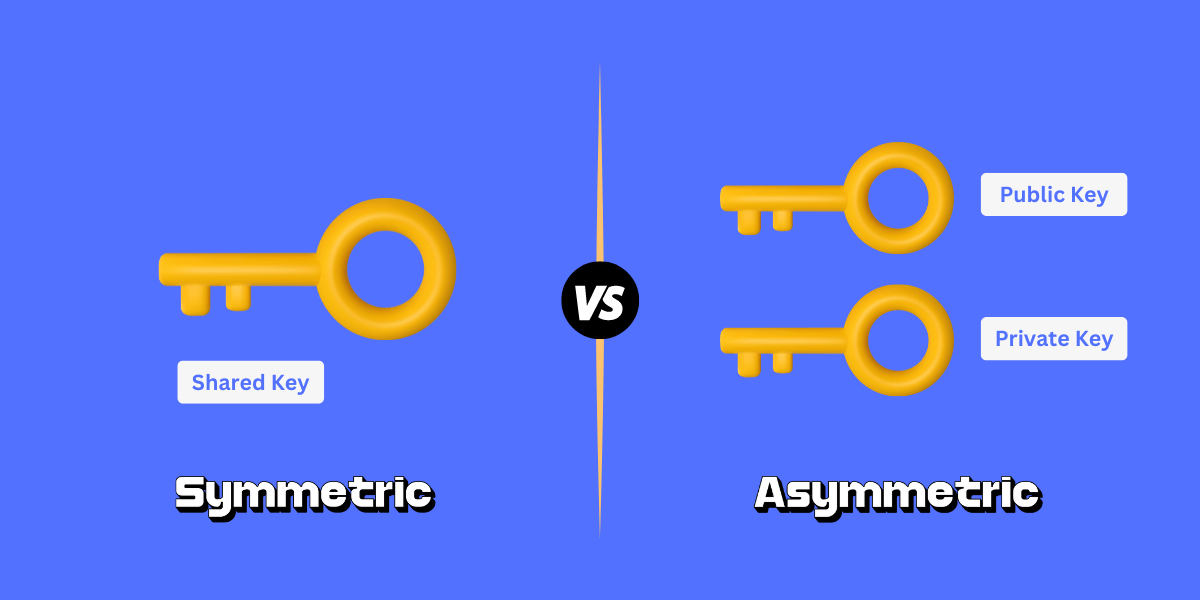
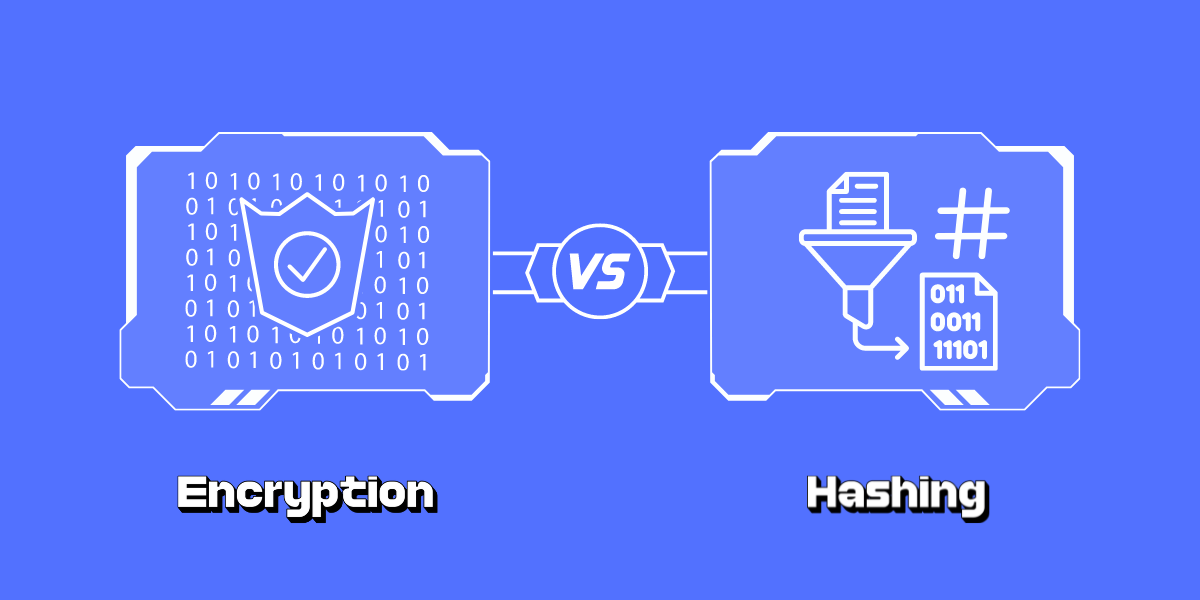
DoS and DDoS Attacks: Differences and How to Prevent A Denial of Service (DoS) attack is a cyber attack that aims to make a website or online service unavailable by overwhelming it with traffic from a single source. A Distributed Denial of Service (DDoS) attack does...