What is Site-to-Site VPN?
A Site-to-Site VPN (Virtual Private Network) connects two or more private networks via the public Internet. It allows users on each private network to access resources on the other private networks as if they were on the same local area network (LAN).
Site-to-site VPNs are commonly used to connect geographically separate offices of an organization into one cohesive network. They provide secure remote access to a corporate network for employees working from outside the office and allow companies to connect securely with business partners and customers.
Key Takeaways
- A site-to-site VPN connects multiple private networks via the public Internet so they can communicate securely.
- It extends a private network across locations, creating one cohesive network. Users can access resources on the other networks as if local.
- Site-to-site VPNs use encryption to secure data and tunneling protocols to encapsulate and direct traffic.
- Companies use site-to-site VPNs to connect remote offices, enable remote access for employees, and securely connect with partners.
- Setting up a site-to-site VPN requires VPN routers or firewalls with VPN capabilities at each location.
How Site-to-Site VPNs Work
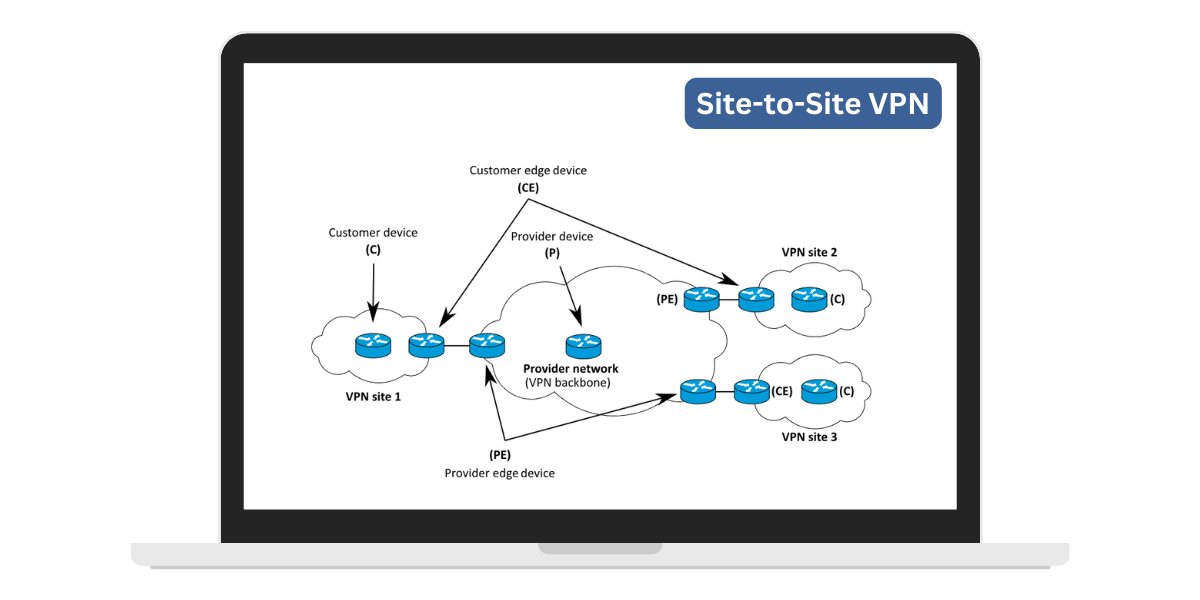
A site-to-site VPN involves connecting the local area networks (LANs) of two or more locations via an encrypted tunnel through the public Internet. It makes two or more physically separate networks function as one virtual network.
Here is an overview of how site-to-site VPNs work:
- VPN routers/firewalls: Each locatiohow-to-use-tor-browser-safelyn has a VPN router, firewall, or security gateway that supports VPN capabilities. This device connects the local network to the VPN tunnel.
- VPN tunnel: An encrypted VPN tunnel is established over the Internet between the VPN devices. Traffic between the networks is routed through this tunnel.
- VPN protocols—Protocols like IPSec, SSL, and others encrypt data and encapsulate traffic flowing through the VPN tunnel.
- Private network access: Users on each network can securely access resources and devices on the other networks through the encrypted VPN tunnel. The remote resources appear as part of the local network.
- Centralized management: VPN policies like access control, firewall rules, and encryption standards can be managed centrally through a VPN management server.
The key aspects of a site-to-site VPN are the encrypted tunnel, the ability to access remote resources as if local, and centralized management. The VPN allows secure communication between multiple locations over the public Internet.
Why Use a Site-to-Site VPN?
There are several reasons organizations use site-to-site VPNs:
- Connect Remote Offices
- Enable Remote Access for Employees
- Connect with Partners and Customers
- Cloud Infrastructure Access
- Network Segmentation and Access Control
- Internet Traffic Encryption
Connect Remote Offices
A multi-location organization can use a site-to-site VPN to interconnect its various offices. This allows users at any location to access resources at any other location through the VPN. Files, databases, apps, and other resources can be accessed securely regardless of geographic distance.
Enable Remote Access for Employees
Site-to-site VPNs allow employees working from home or on the road to access the company network remotely. The employee establishes an encrypted VPN connection from their device to the corporate VPN router/firewall, gaining secure access.
Connect with Partners and Customers
Companies can use site-to-site VPNs to connect securely with business partners, vendors, contractors, and customers. For example, banks use VPNs to connect ATMs to their networks.
Cloud Infrastructure Access
Site-to-site VPNs provide secure access to infrastructure hosted in the cloud, like AWS or Azure. Companies can connect their on-premises networks directly to virtual private clouds.
Network Segmentation and Access Control
Companies can use site-to-site VPNs to connect networks with different security requirements. Access controls can restrict connectivity between specific segments for enhanced security.
Internet Traffic Encryption
Traffic flowing over the public Internet between locations is encrypted via the VPN for enhanced security and privacy, preventing interception or eavesdropping.
Key Components of a Site-to-Site VPN
Several core components work together to create a functional site-to-site VPN:
- VPN Router/Firewall
- VPN Software
- VPN Tunnel
- Encryption Standards
- Authentication Mechanisms
- VPN Protocols
VPN Router/Firewall
A VPN router or firewall with integrated VPN capabilities is required at each location to connect the local network to the VPN tunnel. This device serves as the VPN endpoint. Popular options include:
- Cisco ASA firewalls
- Juniper SRX Series routers
- SonicWall TZ Series
- FortiGate
- pfSense
The VPN router handles encryption, tunnel establishment, access control rules, and routing traffic between the local network and the VPN tunnel.
VPN Software
Software on VPN devices implements VPN protocols and encryption standards. Different platforms support options like IPSec, SSL, OpenVPN, and more. The software packages traffic encrypts it and routes it between endpoints.
VPN Tunnel
The VPN tunnel refers to the pathway formed over the Internet between locations. Traffic between locations is encapsulated and encrypted through this tunnel. It may use protocols like GRE, IPSec, SSL, etc., to establish and maintain the pathway.
Encryption Standards
Encryption ciphers like AES, DES, 3DES, and others encrypt traffic flowing through the VPN tunnel. Both endpoints must use the same standards. Strong 256-bit or higher encryption is recommended for high security.
Authentication Mechanisms
Authentication establishes the identity of users accessing the VPN. It may rely on shared keys, certificates, multi-factor authentication, or directory services like RADIUS for more robust access control.
VPN Protocols
Protocols like IPSec, SSL, IKEv2, OpenVPN, etc., handle encapsulating data, encrypting traffic, and managing the secure VPN pathway between locations.
How to Set Up a Site-to-Site VPN
The general process for deploying a site-to-site VPN involves:
Get Compatible VPN Devices
Obtain a VPN router, firewall, or other security gateway that supports VPN capabilities at each location. Make sure the devices are compatible.
Configure VPN Parameters
You can choose parameters such as the VPN protocol (IPSec, SSL, etc.), encryption ciphers, authentication mechanisms, tunneling mode, etc.
Set Up VPN Tunnels
Configure the VPN connections on each device to establish tunnels with the other endpoints over the Internet.
Define Access Controls
Set access rules determining which devices, networks, and users can communicate through the VPN tunnels.
Test Connectivity
Verify that devices across locations can ping each other and access the allowed resources when connected via VPN.
Maintain and Monitor
Keep VPN software up to date. Monitor traffic flows, user activity, tunnels’ status, and logs to ensure smooth operation.
Configuration specifics vary for different platforms and protocols. However, these general steps provide a framework for deploying a functional VPN that connects locations.
VPN Tunneling Protocols and Encryption
Several key protocols and technologies provide the foundation for site-to-site VPN connectivity:
- IPSec
- SSL/TLS
- MPLS
- AES
- IKE/IKEv2
- OpenVPN
IPSec
IPSec is a popular VPN protocol that operates at the IP layer. It supports multiple encryption standards and modes like tunnel or transport mode. IPSec uses IKE for secure key exchange.
SSL/TLS
SSL and its successor, TLS, are commonly used for site-to-site VPN connectivity. SSL VPNs can provide full network access through tunnels or secure individual connections.
MPLS
Some providers use Multiprotocol Label Switching (MPLS) for managed VPN services. MPLS tunnels traffic across the provider’s WAN between customer sites.
AES
Advanced Encryption Standard (AES) is a symmetric encryption cipher widely used for VPNs. It provides strong security with key lengths from 128 to 256 bits.
IKE/IKEv2
Internet Key Exchange (IKE/IKEv2) protocols handle authentication and secure key exchange between VPN endpoints. This supports establishing IPSec tunnels.
OpenVPN
OpenVPN uses OpenSSL for encryption and allows advanced configurations with multiple protocols and encryption standards.
Choosing the right technologies comes down to vendor support, network characteristics, and security requirements. Robust site-to-site VPNs utilize strong multi-layer encryption and tunneling.
Site-to-Site VPN Use Cases
Some typical use cases for site-to-site VPN connectivity include:
Connect Regional Offices
A company can use a site-to-site VPN to connect its headquarters, satellite offices, and regional branches over the Internet. Employees at any location can collaborate and share resources across sites.
Secure Business Partner Connections
Companies frequently use VPNs to connect securely with suppliers, vendors, advisers, and contractors. For example, a law firm may set up a VPN with a consulting agency it collaborates with on client projects.
Remote Employee Access
Employees on the road or working from home can use VPN clients on their laptops to establish secure connections back to corporate headquarters via site-to-site VPN.
Cloud Infrastructure Access
Site-to-site VPNs are vital for connecting on-premises infrastructure to public cloud environments like AWS, Azure, or Google Cloud. Companies can extend core services securely into the cloud, and site-to-site VPNs provide direct, secure access to virtual private clouds.
Retail and Franchise Networks
Retailers and restaurants use site-to-site VPNs to connect stores back to the corporate network. This allows all locations to access central systems for sales, inventory, supply chain logistics, etc.
ATM and Financial Networks
Banks use VPN technology to provide secure connectivity for ATMs and branch locations back to headquarters. This enables secure financial transactions and access to central accounting systems.
Critical Infrastructure Access
Utilities, energy companies, and other critical infrastructure providers use VPNs to enable secure site-to-site connectivity for industrial control systems across remote locations.
Guest Internet Access
Hotels, conference centers, schools, and other venues use site-to-site VPNs to allow guests temporary secure internet access via hotspots or portals without accessing the internal local network.
IoT Device Connectivity
Manufacturers and other IoT companies can use site-to-site VPNs to secure tunnel IoT devices deployed in the field back to centralized cloud platforms.
As these examples demonstrate, site-to-site VPN use cases span industries like retail, finance, energy, hospitality, manufacturing, and any large distributed organization. The core purpose remains the same: securely interconnecting networks across the Internet.
Site-to-Site VPN vs. Other Options
There are other ways to connect networks aside from site-to-site VPNs:
Leased Lines
Leased lines provide dedicated point-to-point connectivity between sites over private infrastructure. However, leased lines can be extremely expensive compared to VPNs leveraging the public Internet.
MPLS
Multiprotocol Label Switching (MPLS) networks provided by carriers let enterprises build private WANs connecting locations. MPLS offers strong performance and reliability but still incurs service provider costs.
Client VPN
Client VPNs allow individual remote users to access corporate resources and networks. But they don’t directly interconnect networks like site-to-site VPNs do.
Direct Connect
AWS Direct Connect and Azure ExpressRoute allow private, dedicated connections into public cloud environments. However, to connect on-premises infrastructure, site-to-site VPNs are still required.
SD-WAN
Software-defined wide-area networking (SD-WAN) provides an overlay to simplify connecting branch locations. However, SD-WAN still utilizes site-to-site VPNs under the hood.
For most organizations, site-to-site VPNs present the ideal balance of security, performance, reliability, and cost-effectiveness for production network interconnection. The public Internet transports traffic between locations cost-efficiently, while encryption and tunneling provide security.
What are the Main Benefits of Site-to-Site VPN Connectivity
Some top benefits that site-to-site VPNs offer include:
Security
Site-to-site VPNs encrypt data flowing between locations and tunnel traffic through private pathways, enhancing security and privacy over the public Internet.
Remote Access
Users across all locations can access resources on other connected sites as if they were local. VPN extends the network to enable universal connectivity.
Cost Savings
Utilizing the public Internet for transport avoids expensive leased lines or managed MPLS services. Site-to-site VPN offers a cost-effective WAN.
Reliability
Modern site-to-site VPNs offer excellent uptime and reliability to keep remote locations constantly interconnected.
Scalability
It’s easy to add and remove site connections from a VPN as needs evolve. VPNs enable scalable growth and flexibility.
Centralized Control
VPN policies like access rules and encryption standards can be managed centrally for consistent security across all sites.
Platform Compatibility
Standards-based VPN protocols allow multivendor interoperability between various routers, firewalls, and endpoint operating systems.
High Performance
Thanks to efficient protocols and ample internet capacity, site-to-site VPNs typically offer ample bandwidth, low latency, and high throughput.
For connecting networks over distance, site-to-site VPNs deliver one of the most versatile, secure, and cost-effective connectivity options available.
Common Misconceptions About Site-to-Site VPNs
Some common misconceptions about site-to-site VPN technology include:
VPNs Degrade Performance
Thanks to efficient protocols and broadband capacity, modern VPNs have minimal impact on throughput and latency. They do not bog down connections.
VPN Use is Suspicious
VPN adoption is mainstream across enterprises and very legitimate. The majority of organizations rely on VPNs for remote access and interconnection.
VPNs Are Too Complex
While thorough planning and configuration are required, VPN technology itself is well-established and robust. Many platforms include wizards or templates to simplify deployment.
VPNs Aren’t Secure Enough
Utilizing strong multi-layer encryption, VPNs provide rock-solid security that meets or exceeds most corporate requirements.
VPNs Are Only For Remote Access
While VPNs excel at remote access, site-to-site connectivity between locations is one of their top uses among enterprises.
VPNs Are Too Expensive
Hardware and licensing costs make affordable VPN solutions accessible even for small businesses. They are far cheaper than old leased line connectivity.
VPNs Can Bypass Geographic Restrictions
Using VPNs explicitly to circumvent content filtering or geographic access restrictions may constitute abuse in some cases. Responsible usage is expected.
Modern site-to-site VPN technology’s capabilities and flexibility make it an essential component of network infrastructure and remote connectivity for organizations of all sizes.
Final Thoughts
In conclusion, a site-to-site VPN is a crucial technology for securely connecting geographically distributed networks. By establishing an encrypted tunnel between remote locations, it allows for the safe transmission of sensitive data, enabling businesses to securely share resources, collaborate, and centralize management.
The process involves authenticating the endpoints, encrypting the traffic, and maintaining the connection, all while providing the benefits of a private network over the public internet. As organizations continue to expand their operations and rely on distributed infrastructure, the site-to-site VPN remains an indispensable tool for ensuring the confidentiality, integrity, and accessibility of their critical information.
Frequently Asked Questions About Site-to-Site VPNs
What is a site-to-site VPN used for?
Site-to-site VPNs securely connect multiple office locations, enable remote access for employees, securely connect to the cloud, and link infrastructure with business partners over the public Internet.
How does a site-to-site VPN work?
It works by establishing encrypted tunnels between VPN routers at each location to connect LANs. This allows clients at any site to access resources from the other sites as if directly connected locally.
What is the difference between site-to-site and client VPNs?
Site-to-site VPNs connect entire networks, while client VPNs only provide individual device access. Client VPNs are used for remote access into a corporate network.
What equipment do you need for a site-to-site VPN?
You need VPN-capable routers, firewalls, or other security gateways at each location to serve as VPN endpoints and tunnel traffic between sites.
How secure are site-to-site VPN connections?
Site-to-site VPNs use advanced encryption and tunneling to provide highly secure connectivity between locations over the public Internet. SSL and IPSec VPNs support 256-bit AES and other strong ciphers.
What is the difference between IPSec and SSL VPNs?
IPSec operates at the network layer, while SSL works at the session layer. IPSec provides full network access, while SSL can be limited to specific apps. SSL tends to be simpler to configure.
Is a site-to-site VPN the same as an MPLS network?
No, MPLS refers to Multiprotocol Label Switching networks built by carriers to interconnect customer sites. Site-to-site VPNs provide similar capabilities but are delivered over the public Internet.
What are the components of a site-to-site VPN solution?
Key components include VPN routers/firewalls, VPN tunneling protocols like IPSec or SSL, encryption standards like AES, authentication mechanisms like RADIUS, and, in some cases, centralized VPN management servers.
How can I monitor and troubleshoot my site-to-site VPN?
Monitoring tools can track tunnel status, traffic flows, and system logs. Packet captures, interface statistics and ping tests help troubleshoot issues like tunnel failures, slow connectivity, or routing problems.

Jinu Arjun
 Verified Experienced Content Writer
Verified Experienced Content Writer
Jinu Arjun is an accomplished content writer with over 8+ years of experience in the industry. She currently works as a Content Writer at EncryptInsights.com, where she specializes in crafting engaging and informative content across a wide range of verticals, including Web Security, VPN, Cyber Security, and Technology.